
How To: Top 10 Exploit Databases for Finding Vulnerabilities
What Is a CVE?
The numbered reference system used to catalog disclosed vulnerabilities and exploits is called the Common Vulnerabilities and Exposures (CVE) system.For example, the Exploit Database uses CVEs to identify individual vulnerabilities which are associated with a particular version of a service like "SSH v7.7," as shown below with CVE-2018-15473. All exploit databases operate and index CVEs similarly or exactly like the CVE number assigned to this particular SSH username enumeration vulnerability.
- Don't Miss: How to Easily Detect CVEs with Nmap Scripts
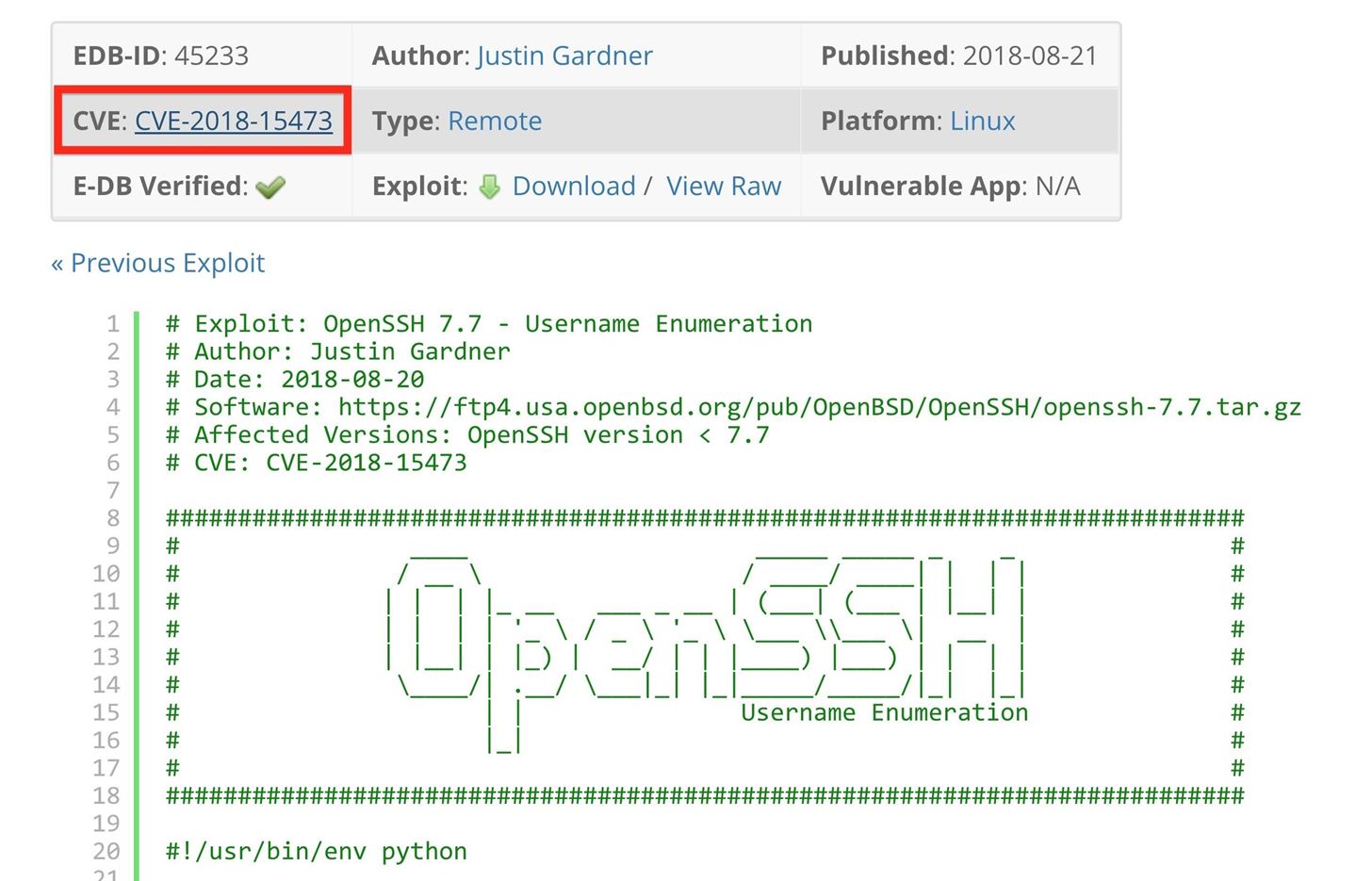
Now that we know what a CVE is, let's see where we can find them.
1. CIRCL
The Computer Incident Response Center Luxembourg (CIRCL) is an information security organization designed to handle cyber threat detections and incidents. Its website features security research publications and a searchable CVE database.
2. VulDB
For decades, the VulDB specialists have coordinated with large and independent information security communities to compile a searchable database of over 124,000 CVEs. Hundreds of new entries are added on a daily basis and scored (e.g., low, medium, high) based on the severity of the disclosed exploit.
3. SecurityFocus
SecurityFocus has reported on cybersecurity incidents and published whitepapers in the past. These days, it tracks software bug reports and has been compiling a searchable archive of CVEs since 1999.
4. 0day.today
0day.today (accessible via tor onion service), is an exploit database that also sells private exploits for as much as $5,000 USD. While there are several reports of scams occurring with private sales, the searchable public database is quite legitimate.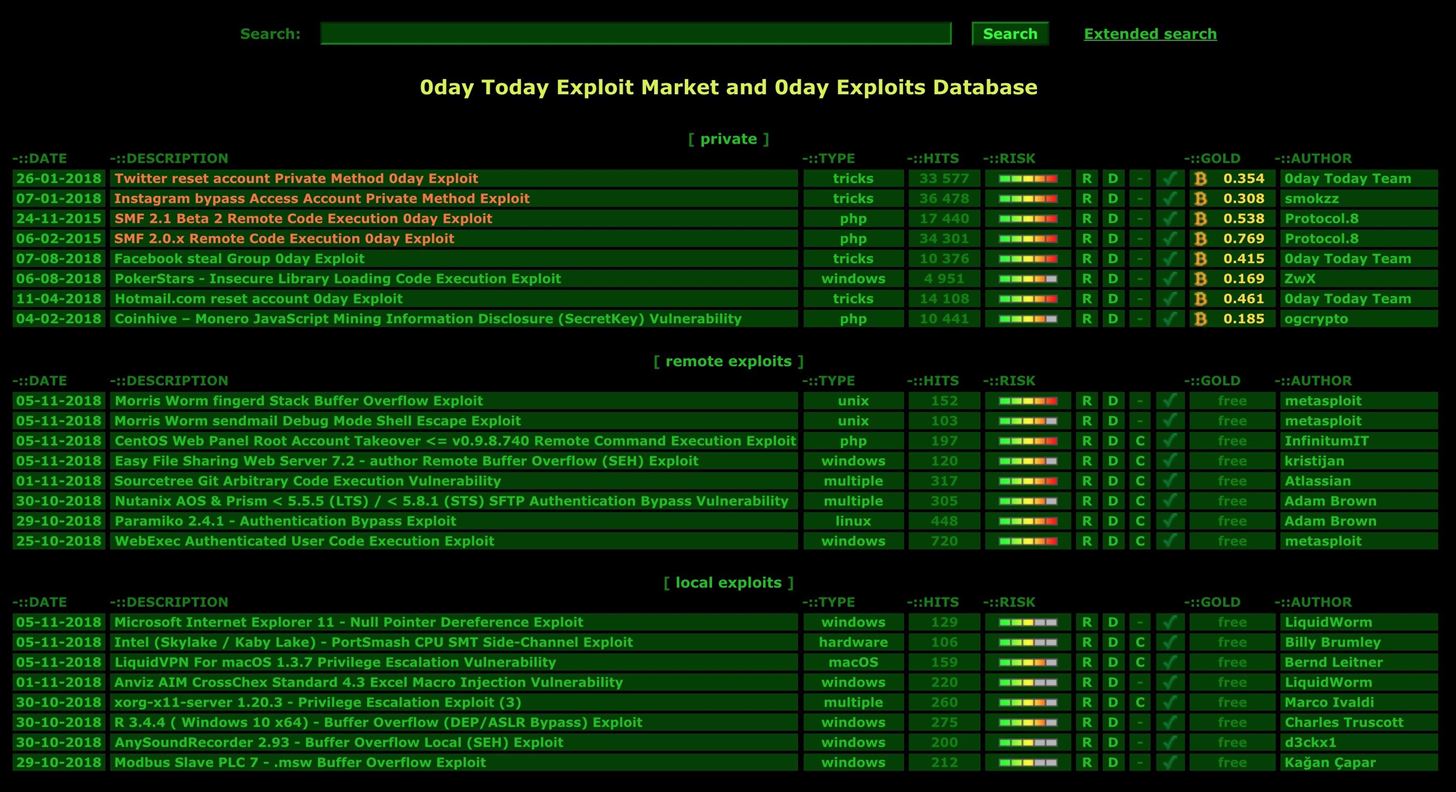
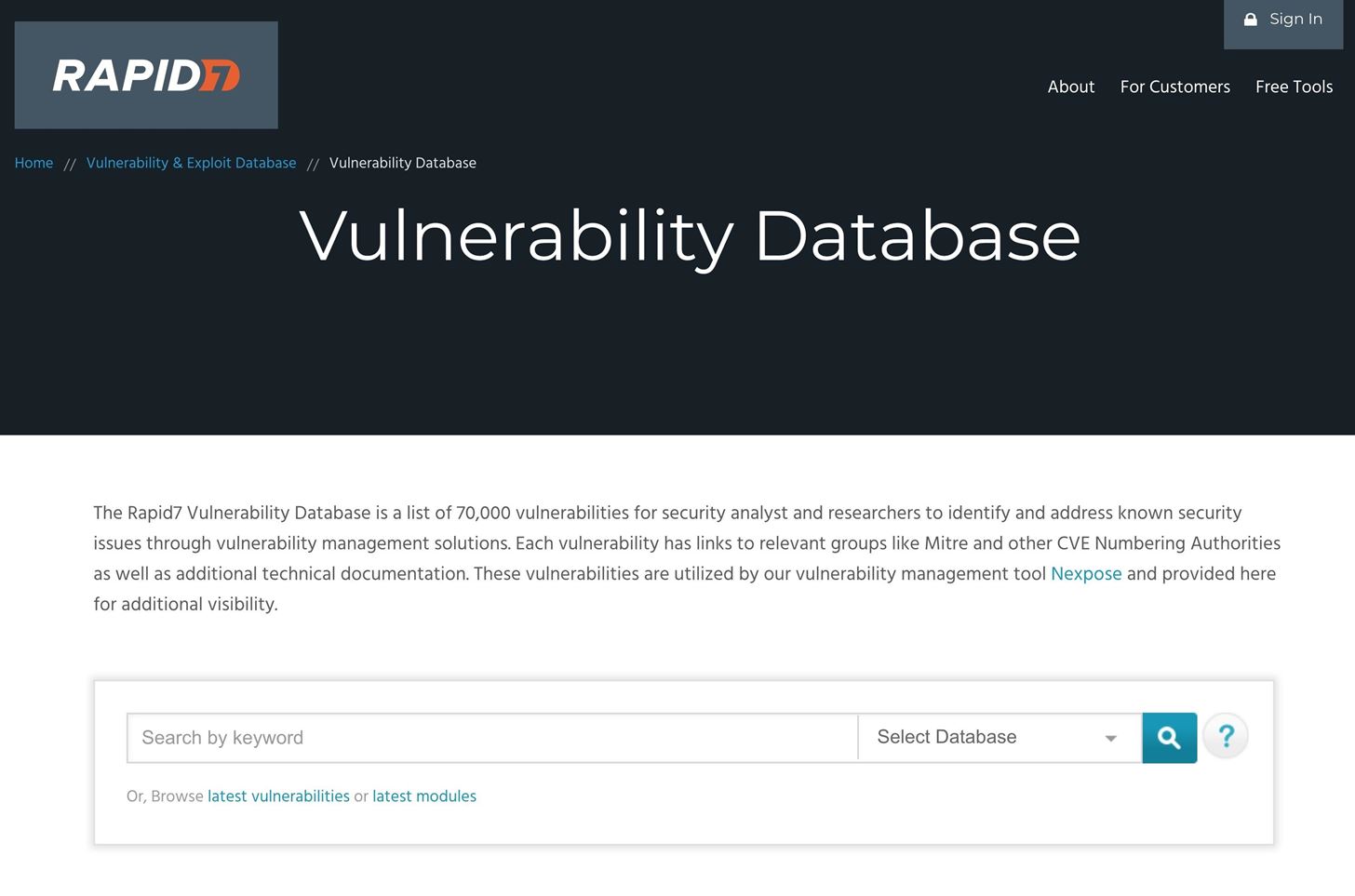
5. Rapid7
Rapid7, creators of the Metasploit Framework, have a searchable CVE database on its website. However, unlike other databases, Rapid7 very rarely features the actual exploit code. Instead, it offers advisories containing helpful reference links to relevant documentation for remediation, as well as links to msfconsole modules that automate the indexed exploit.For example, since the public disclosure of CVE-2018-15473, the aforementioned SSH username enumeration exploit, the hack can be found in msfconsole and executed with great ease.
6. NIST
The National Institute of Standards and Technology (NIST) is one of the oldest physical science laboratories in the United States. It's currently involved in a myriad of technologies and research such as its national initiative for cybersecurity education, CVE archive, cutting-edge technology news, and quantum information science program. Anyone can search its CVE database.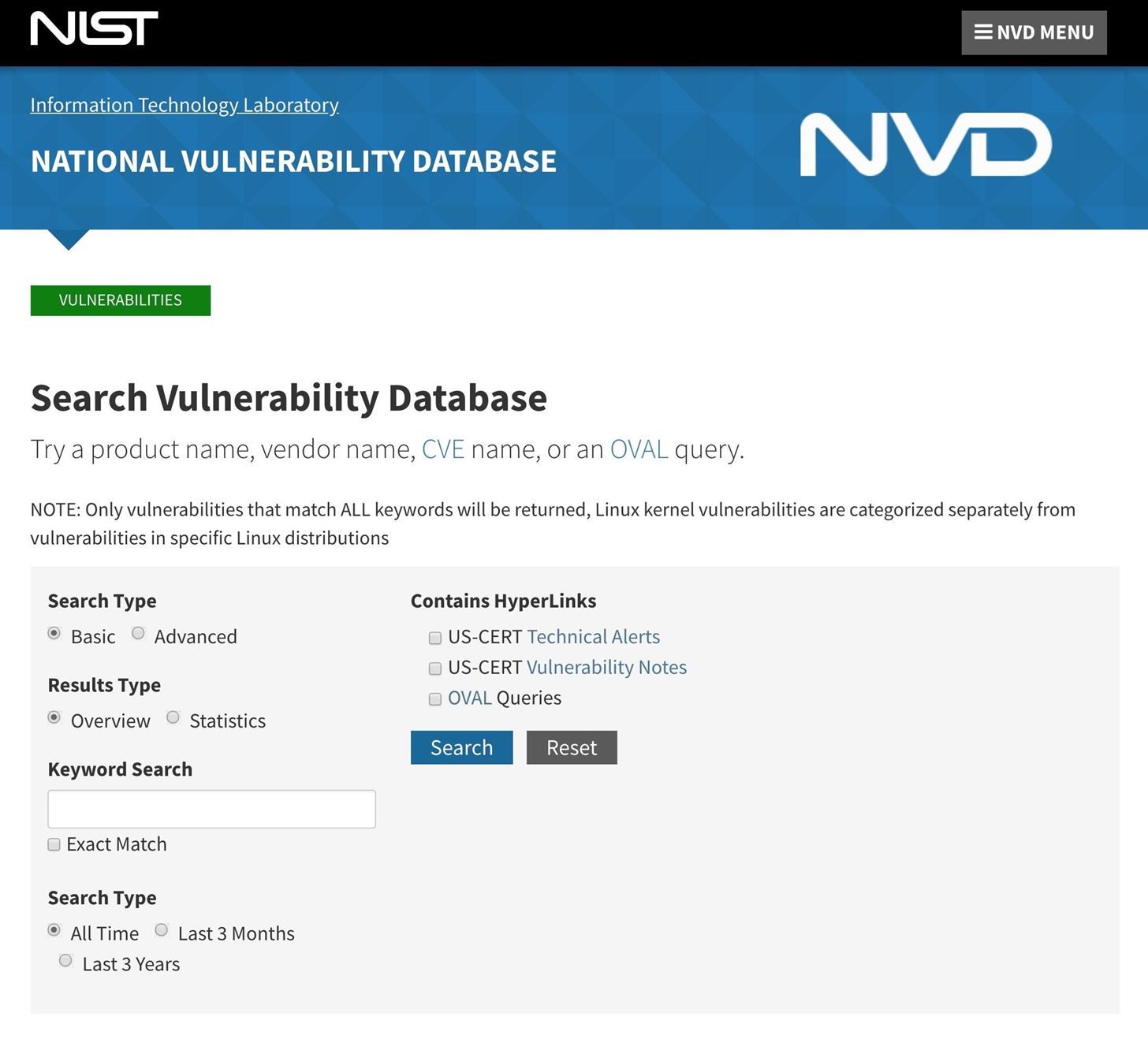
7. Packet Storm Security
Packet Storm Security isn't exactly intended to be a searchable database of exploits. Rather, it's a general resource of information pertaining to vulnerability advisories and remediations. The Packet Storm website also features hacker news, research whitepapers, and a feed of recently disclosed CVEs.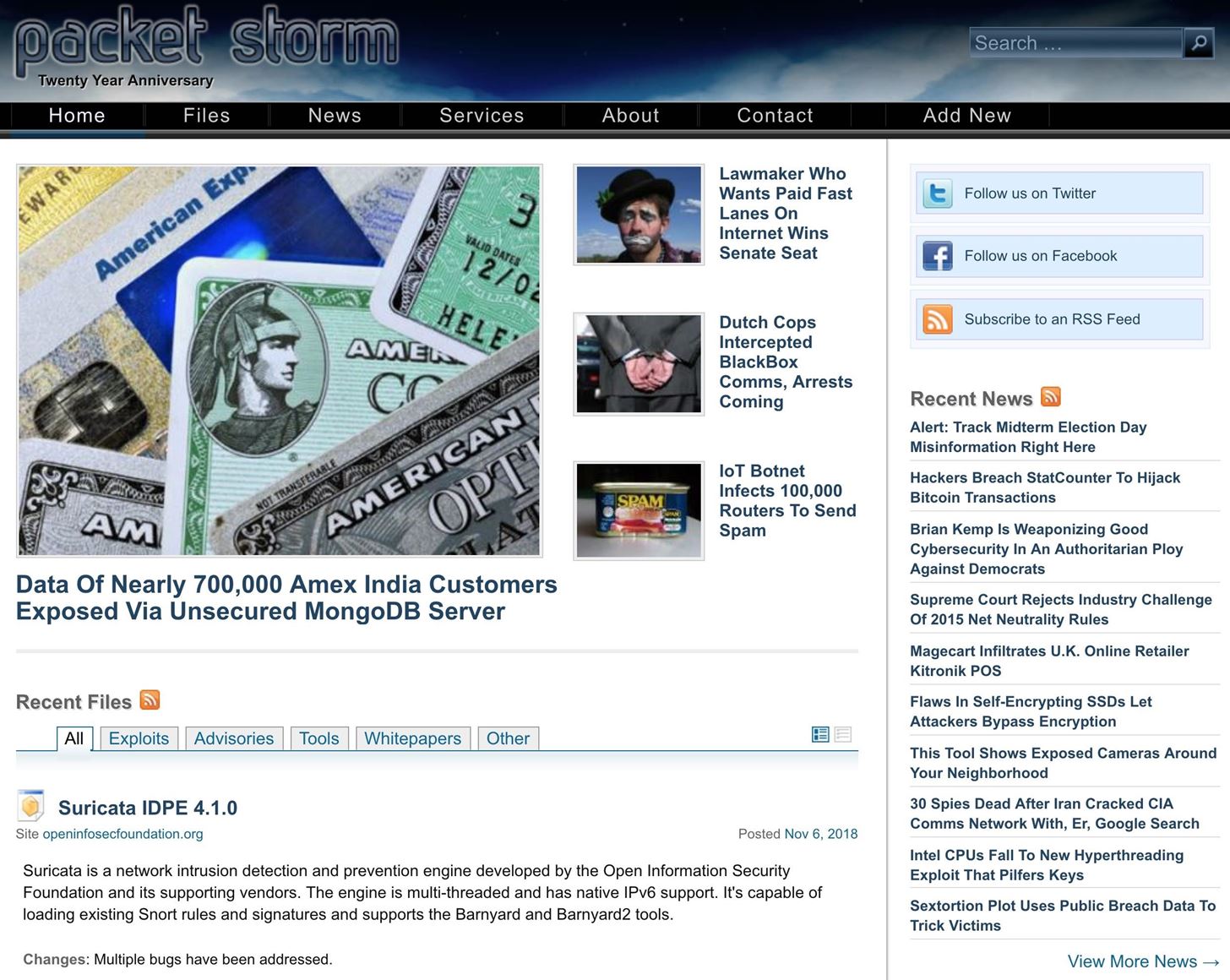
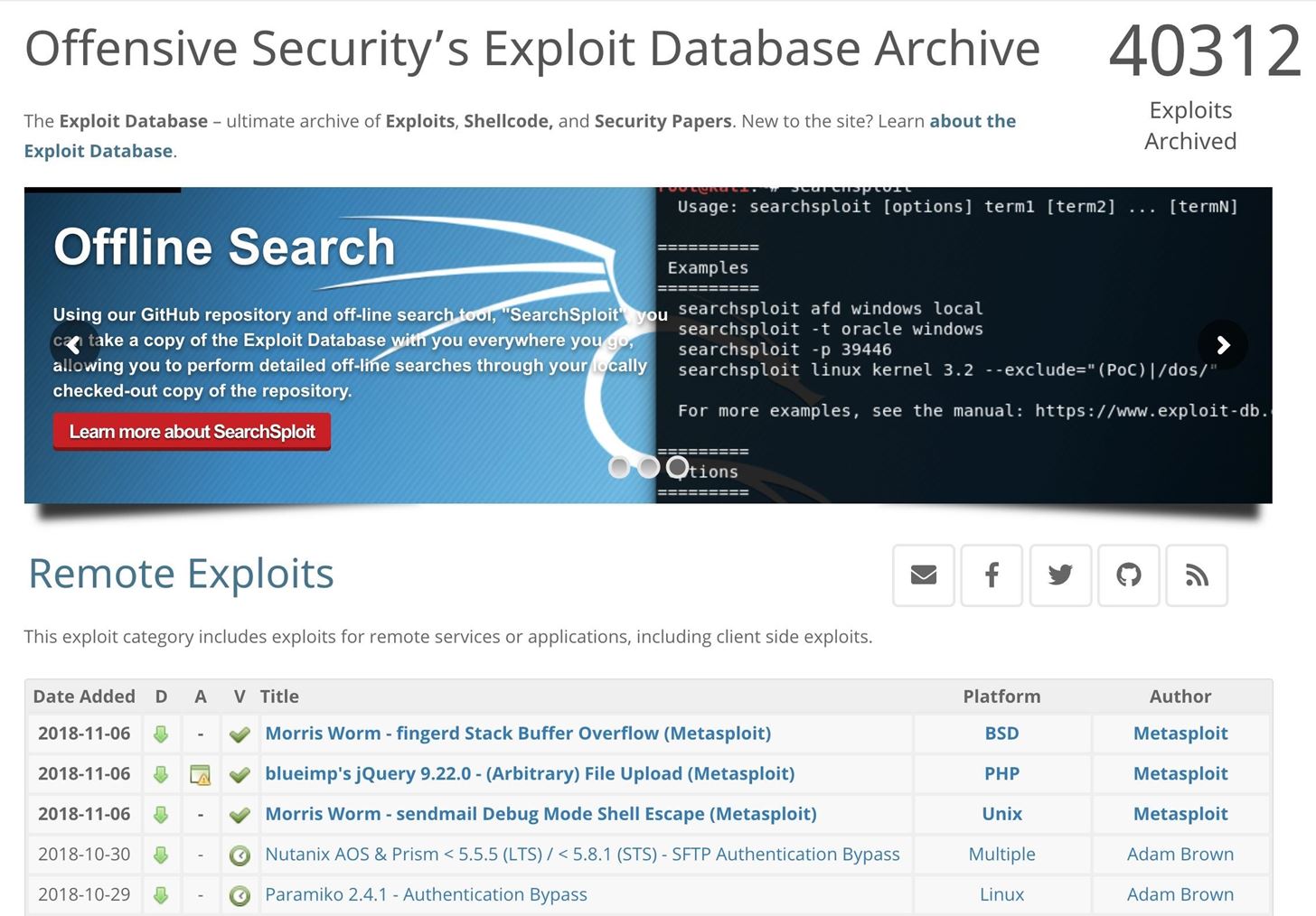
8. Exploit Database
The Exploit Database is currently maintained by the Offensive Security organization which specializes in advanced Windows exploitation, web application security, and various prominent penetration tester certification training.Its searchable database currently features a collection of over 40,000 remote, local, web application, and denial-of-service exploits, as well as a Google hacking database, research whitepapers, and a database search function.
9. Vulners
Vulners, founded by Kir Ermakov, is a CVE database currently containing over 176,500 indexed exploits. Its website includes CVE statistics, a Linux vulnerability management auditor, and searchable CVE database.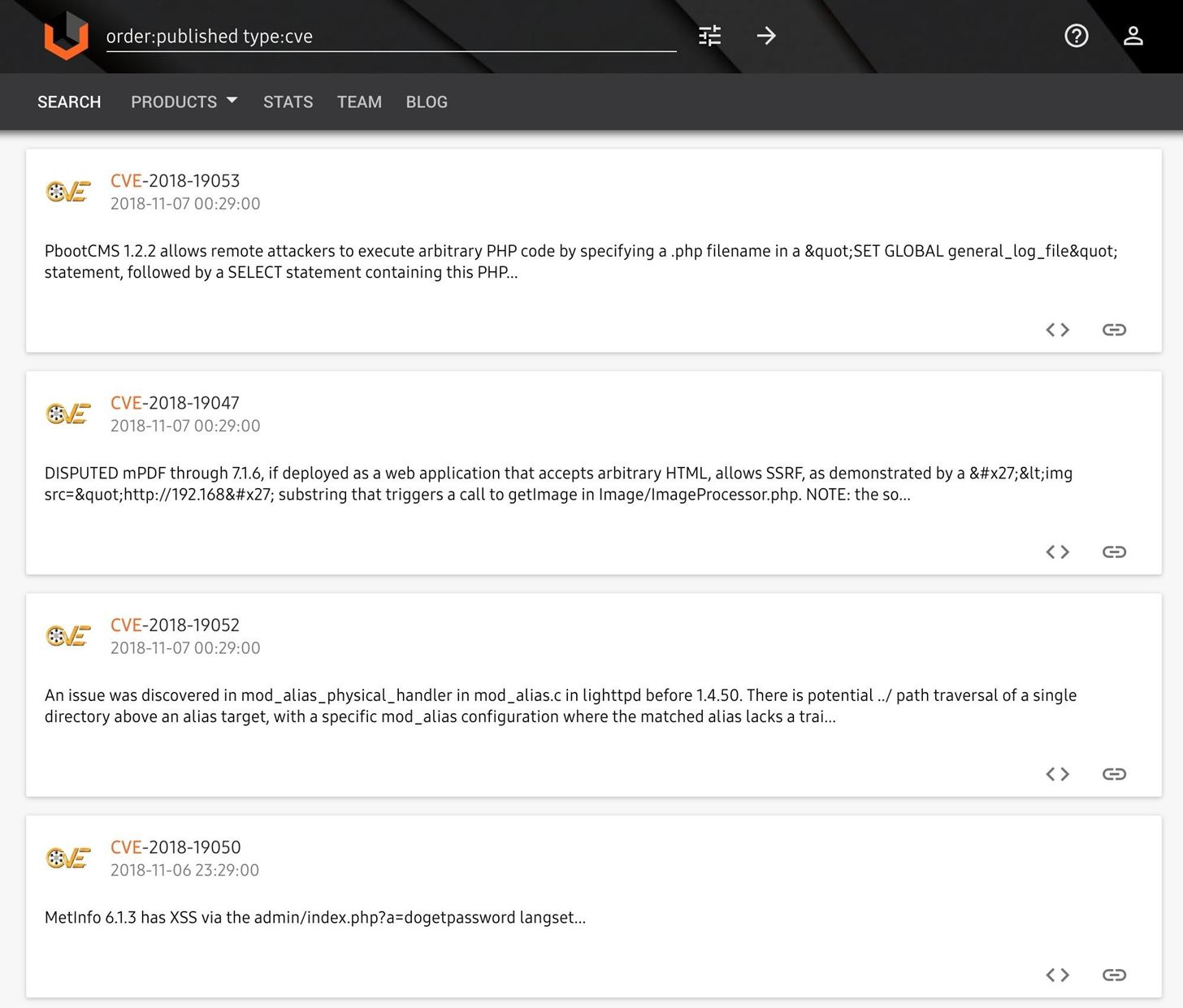
10. MITRE
MITRE is a US government-sponsored organization that manages federally funded research and development centers (FFRDC). Its website emphasizes commercial publications and information related to their FFRDCs such as the National Cybersecurity program. It also maintains one of the biggest and widely referenced CVE databases currently available, searchable by the public.
Operating System Advisory & CVE Databases (Bonus)
Some readers may be looking to explore recent OS-specific vulnerabilities — or simply trying to remain aware to better protect themselves. Most operating system distributions offer an advisory listing on their website. These are mostly application-specific vulnerabilities and bugs, but in many cases, can be easily exploited by attackers.- Microsoft: Windows Security Update Guide
- Android: Monthly Security Bulletin
- Apple: Security Updates
- Ubuntu: Security Notices, CVE Tracker, Mailing List
- Debian: Recent Advisories, Mailing List
- RedHat: CVE Database, Security Advisories
- Arch Linux: Security Advisories
- Hot
- Latest
-
 How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
-
 How To:
Probe Websites for Vulnerabilities More Easily with the TIDoS Framework
How To:
Probe Websites for Vulnerabilities More Easily with the TIDoS Framework
-
 How To:
Steal Usernames & Passwords Stored in Firefox on Windows 10 Using a USB Rubber Ducky
How To:
Steal Usernames & Passwords Stored in Firefox on Windows 10 Using a USB Rubber Ducky
-
 How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
-
 How To:
4 Ways to Crack a Facebook Password & How to Protect Yourself from Them
How To:
4 Ways to Crack a Facebook Password & How to Protect Yourself from Them
-
 Hack Like a Pro:
How to Secretly Hack Into, Switch On, & Watch Anyone's Webcam Remotely
Hack Like a Pro:
How to Secretly Hack Into, Switch On, & Watch Anyone's Webcam Remotely
-
 How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
-
 How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
-
 How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
-
 How To:
Top 10 Things to Do After Installing Kali Linux
How To:
Top 10 Things to Do After Installing Kali Linux
-
 How To:
Compromise a Web Server & Upload Files to Check for Privilege Escalation, Part 2
How To:
Compromise a Web Server & Upload Files to Check for Privilege Escalation, Part 2
-
 How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
-
 Hack Like a Pro:
How to Hack Facebook (Facebook Password Extractor)
Hack Like a Pro:
How to Hack Facebook (Facebook Password Extractor)
-
 How To:
Get Unlimited Free Trials Using a "Real" Fake Credit Card Number
How To:
Get Unlimited Free Trials Using a "Real" Fake Credit Card Number
-
 How To:
Crack Any Master Combination Lock in 8 Tries or Less Using This Calculator
How To:
Crack Any Master Combination Lock in 8 Tries or Less Using This Calculator
-
 How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
-
 How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
-
 How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
-
 How To:
Crack Wi-Fi Passwords with Your Android Phone and Get Free Internet!
How To:
Crack Wi-Fi Passwords with Your Android Phone and Get Free Internet!
-
 How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
-
 How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
How To:
Discover & Attack Raspberry Pis Using Default Credentials with Rpi-hunter
-
 How To:
Probe Websites for Vulnerabilities More Easily with the TIDoS Framework
How To:
Probe Websites for Vulnerabilities More Easily with the TIDoS Framework
-
 How To:
Steal Usernames & Passwords Stored in Firefox on Windows 10 Using a USB Rubber Ducky
How To:
Steal Usernames & Passwords Stored in Firefox on Windows 10 Using a USB Rubber Ducky
-
 How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
-
 How To:
4 Ways to Crack a Facebook Password & How to Protect Yourself from Them
How To:
4 Ways to Crack a Facebook Password & How to Protect Yourself from Them
-
 Hack Like a Pro:
How to Secretly Hack Into, Switch On, & Watch Anyone's Webcam Remotely
Hack Like a Pro:
How to Secretly Hack Into, Switch On, & Watch Anyone's Webcam Remotely
-
 How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
How to Hack Wi-Fi:
Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher
-
 How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
How To:
Use & Abuse the Address Resolution Protocol (ARP) to Locate Hosts on a Network
-
 How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
-
 How To:
Top 10 Things to Do After Installing Kali Linux
How To:
Top 10 Things to Do After Installing Kali Linux
-
 How To:
Compromise a Web Server & Upload Files to Check for Privilege Escalation, Part 2
How To:
Compromise a Web Server & Upload Files to Check for Privilege Escalation, Part 2
-
 How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
How To:
Build a Beginner Hacking Kit with the Raspberry Pi 3 Model B+
-
 Hack Like a Pro:
How to Hack Facebook (Facebook Password Extractor)
Hack Like a Pro:
How to Hack Facebook (Facebook Password Extractor)
-
 How To:
Get Unlimited Free Trials Using a "Real" Fake Credit Card Number
How To:
Get Unlimited Free Trials Using a "Real" Fake Credit Card Number
-
 How To:
Crack Any Master Combination Lock in 8 Tries or Less Using This Calculator
How To:
Crack Any Master Combination Lock in 8 Tries or Less Using This Calculator
-
 How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
-
 How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
How To:
Buy the Best Wireless Network Adapter for Wi-Fi Hacking in 2019
-
 How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
-
 How To:
Crack Wi-Fi Passwords with Your Android Phone and Get Free Internet!
How To:
Crack Wi-Fi Passwords with Your Android Phone and Get Free Internet!
-
 How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
















Be the First to Comment
Share Your Thoughts