Absolute Uninstaller 1.3
By: Gabri3l / ARTehttp://cracking.accessroot.com
Hardcoded Serial & Serial Check Routine
The Target:
Glarysoft Absolute Uninstaller 1.3
http://dl.winsite.com/bin/downl?22000000036543
http://rapidshare.de/files/6848829/uninstaller.exe.html
The Tools:
Ollydbg 1.10
The Protection:
Custom Serial Protection
Other Information:
We are going to learn about hardcoded serials and the serial checking routine. Hardcoded serials are not calculated based on your user name. Instead they are serials that are written into the program and can be found by doing a string search. The program we are going to use to demonstrate this is Absolute Uninstaller 1.3 developed by hxxp://www.glarysoft.com/
This is actually a pretty decent program so I stress, as always, if you like it or plan on using it commercially please purchase it.
This tutorial is for an older version of the program than the one currently released. At the end of the tutorial I will cover how to crack the newer version of this program. At the time this tutorial was written; patching lockdll.dll in this manner would allow you to "register" ALL glarysoft products.
Absolute Uninstaller 1.3
By: Gabri3l / ARTeam
http://cracking.accessroot.com
Hardcoded Serial & Serial Check Routine
The Target:
Glarysoft Absolute Uninstaller 1.3
http://dl.winsite.com/bin/downl?22000000036543
http://rapidshare.de/files/6848829/uninstaller.exe.html
The Tools:
Ollydbg 1.10
The Protection:
Custom Serial Protection
Other Information:
We are going to learn about hardcoded serials and the serial checking routine. Hardcoded serials are not calculated based on your user name. Instead they are serials that are written into the program and can be found by doing a string search. The program we are going to use to demonstrate this is Absolute Uninstaller 1.3 developed by hxxp://www.glarysoft.com/
This is actually a pretty decent program so I stress, as always, if you like it or plan on using it commercially please purchase it.
This tutorial is for an older version of the program than the one currently released. At the end of the tutorial I will cover how to crack the newer version of this program. At the time this tutorial was written; patching lockdll.dll in this manner would allow you to "register" ALL glarysoft products.
Best viewed in Firefox at 1280x1024
Intro:
All the tools you will need can be found online:
http://home.t-online.de/home/Ollydbg/
Body: |
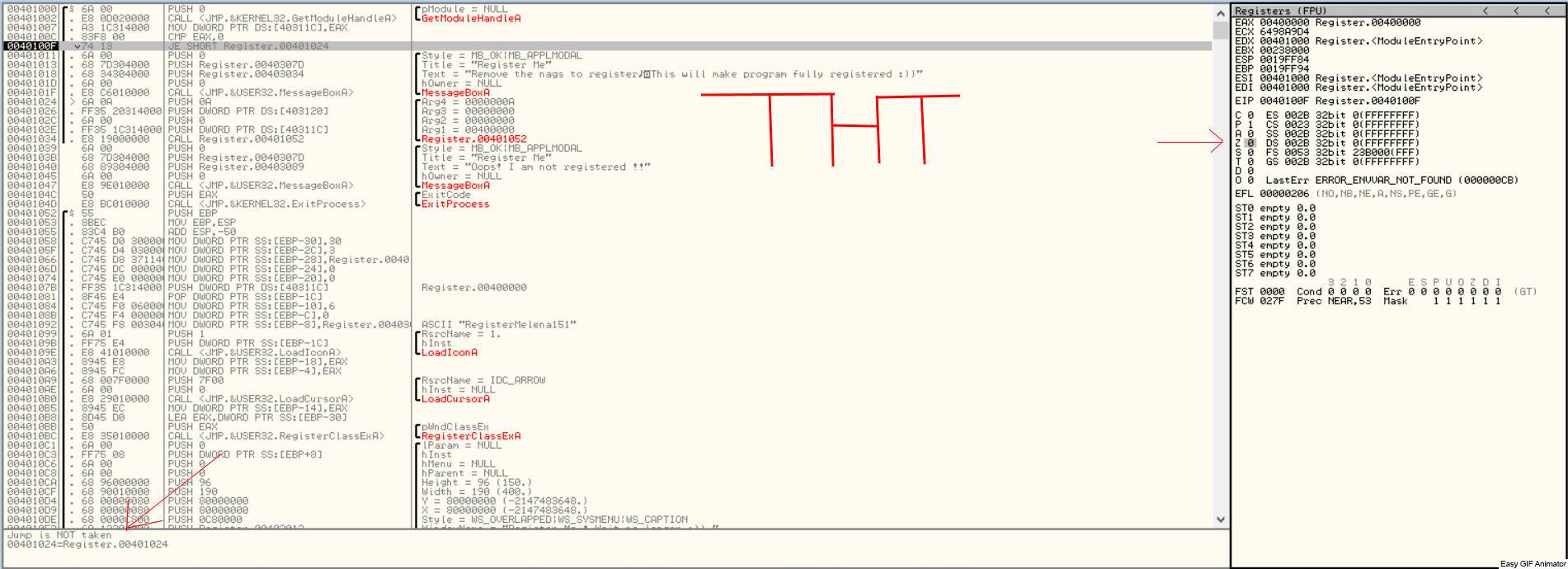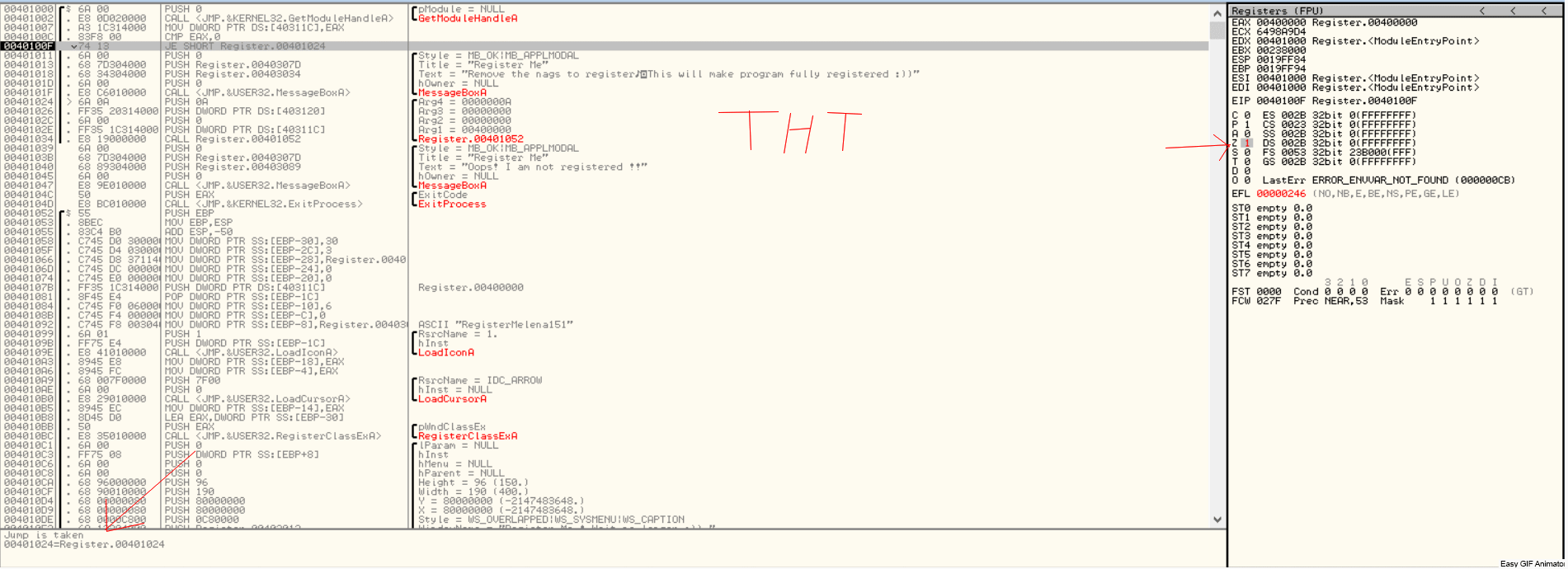
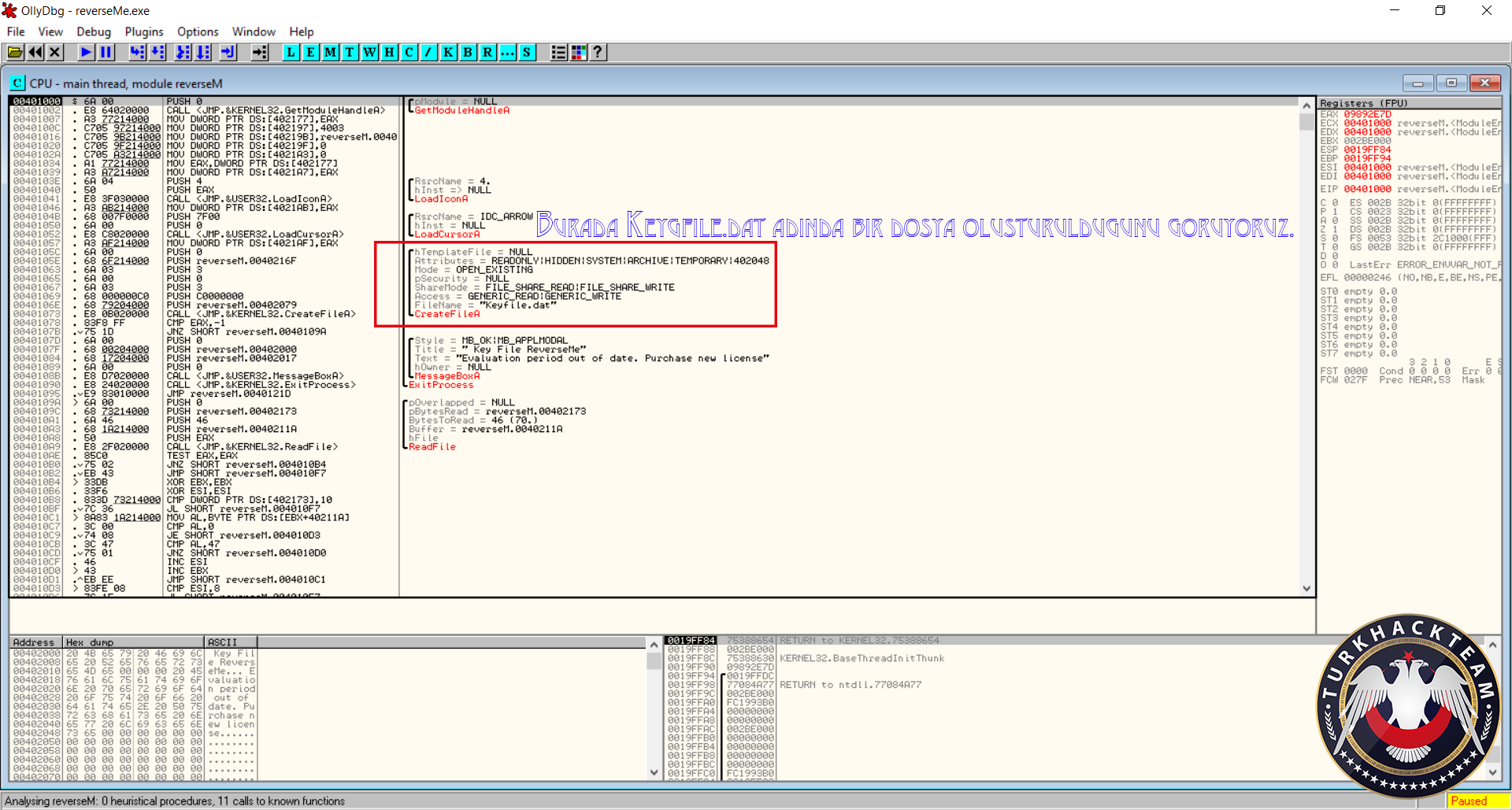
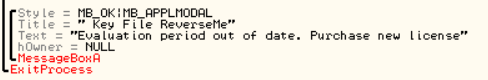
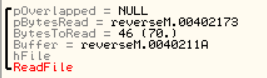
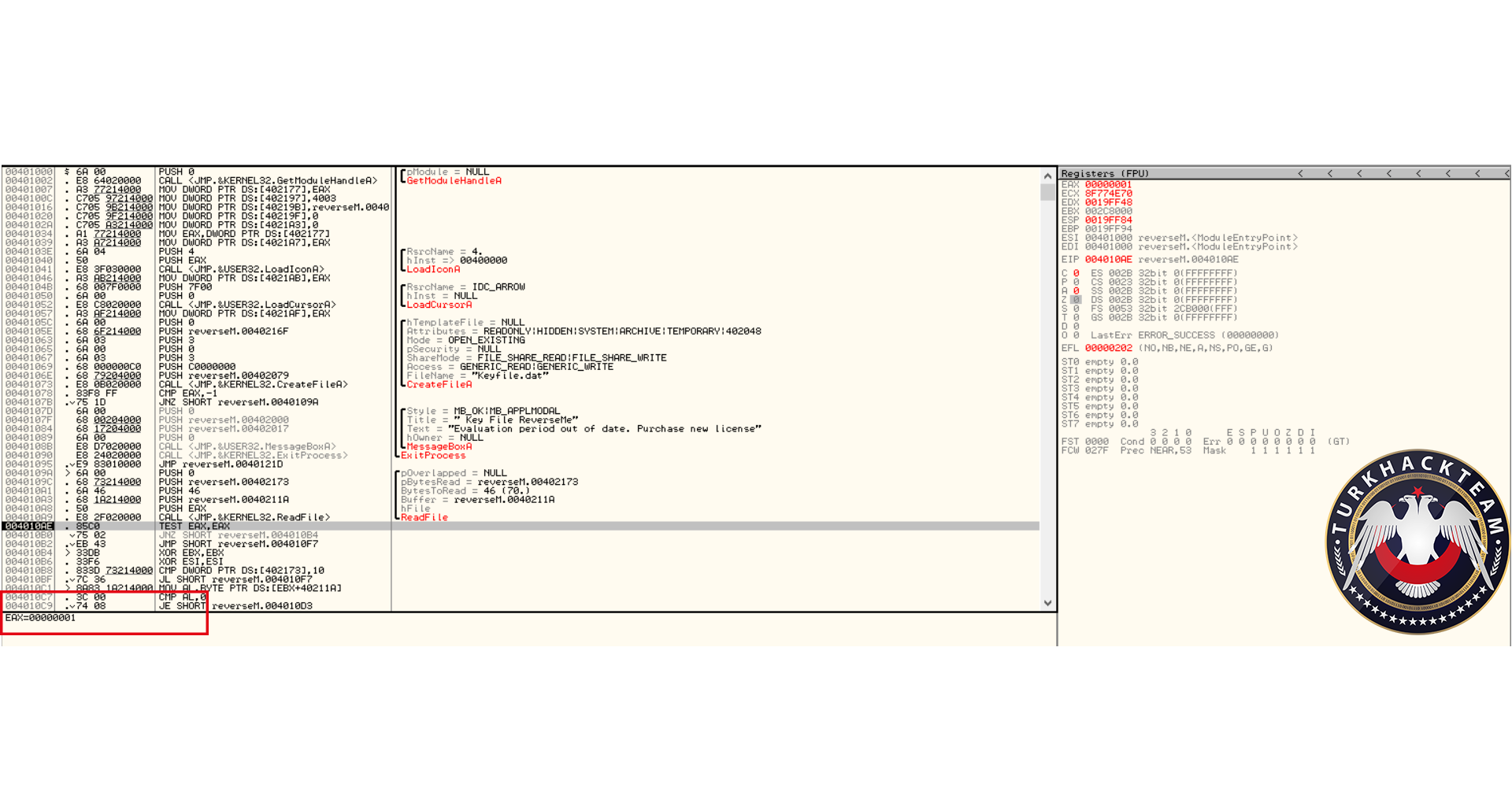
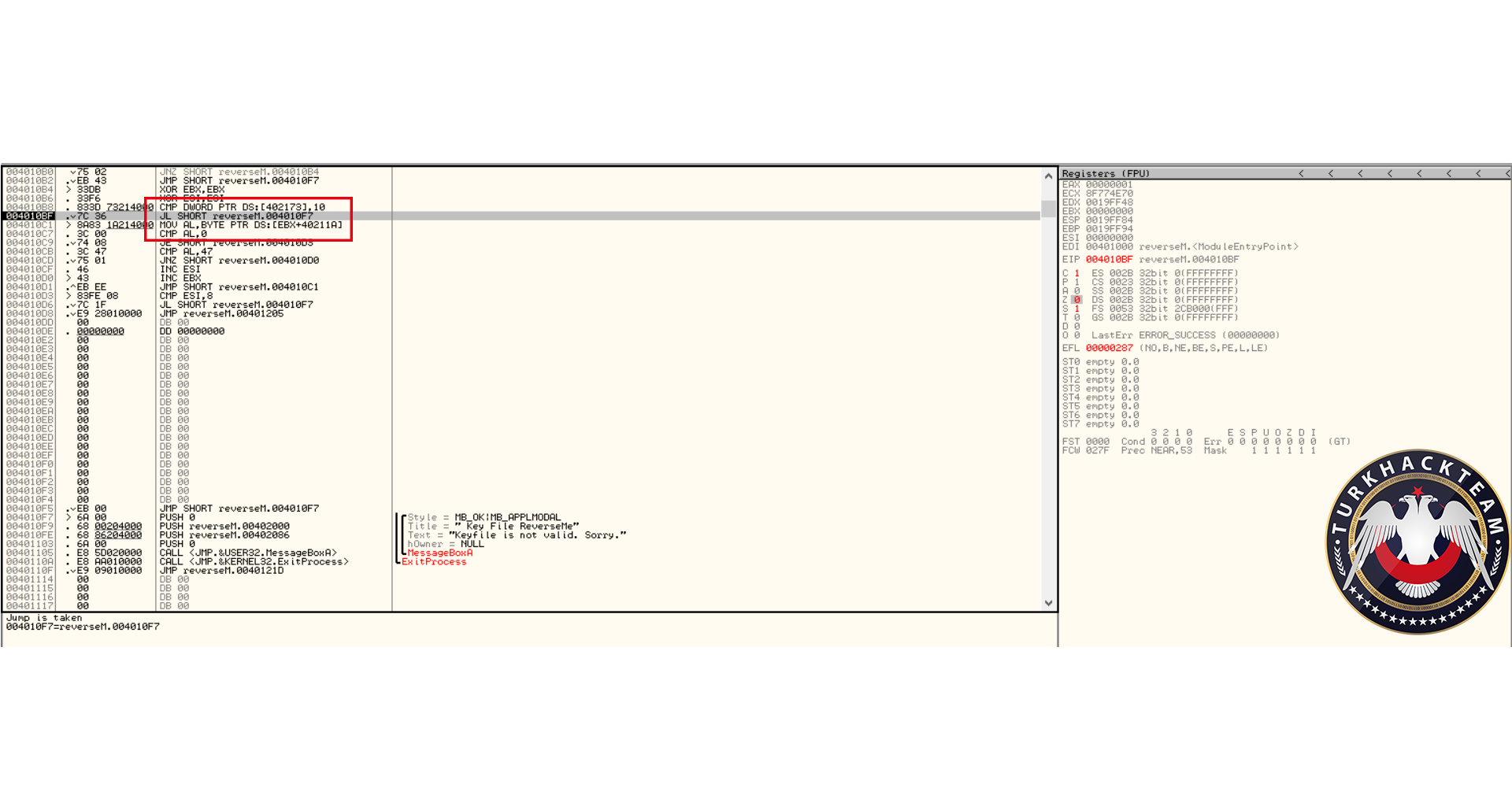
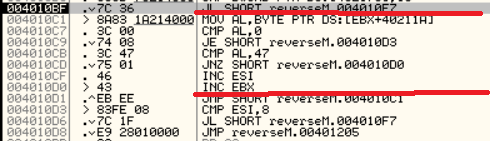
Defeating Hardcoded Serial Protection: 1. First thing we always do is test the program out. Run the program and you will be presented with a nag screen telling you that you are on day 1 of 30. Press the Enter Code button and enter any name and serial into the box. Press Okay, and you will see "The Registration code you have entered is invalid". Write this down, and close the program. CODE 004E0AB8 > $ 55 PUSH EBP 004E0AB9 . 8BEC MOV EBP,ESP 004E0ABB . 83C4 EC ADD ESP,-14 004E0ABE . 53 PUSH EBX 004E0ABF . 56 PUSH ESI 004E0AC0 . 33C0 XOR EAX,EAX 004E0AC2 . 8945 EC MOV DWORD PTR SS:[EBP-14],EAX 004E0AC5 . B8 58074E00 MOV EAX,uninstal.004E0758 004E0ACA . E8 355AF2FF CALL uninstal.00406504 004E0ACF . 33C0 XOR EAX,EAX 004E0AD1 . 55 PUSH EBP 004E0AD2 . 68 E20B4E00 PUSH uninstal.004E0BE2 004E0AD7 . 64:FF30 PUSH DWORD PTR FS:[EAX] 004E0ADA . 64:8920 MOV DWORD PTR FS:[EAX],ESP 004E0ADD . 8D55 EC LEA EDX,DWORD PTR SS:[EBP-14] 004E0AE0 . B8 01000000 MOV EAX,1 004E0AE5 . E8 CA1FF2FF CALL uninstal.00402AB4 004E0AEA . 8B45 EC MOV EAX,DWORD PTR SS:[EBP-14] 004E0AED . BA F80B4E00 MOV EDX,uninstal.004E0BF8 ; ASCII "reg" 004E0AF2 . E8 953BF2FF CALL uninstal.0040468C 004E0AF7 . 0F84 9F000000 JE uninstal.004E0B9C 004E0AFD . C605 584E4E00 >MOV BYTE PTR DS:[4E4E58],0 004E0B04 . 68 FC0B4E00 PUSH uninstal.004E0BFC ; /FileName = "lockdll.dll" 004E0B09 . E8 565EF2FF CALL <JMP.&kernel32.LoadLibraryA> ; \LoadLibraryA 004E0B0E . A3 544E4E00 MOV DWORD PTR DS:[4E4E54],EAX 004E0B13 . 33C0 XOR EAX,EAX 004E0B15 . 55 PUSH EBP 004E0B16 . 68 8C0B4E00 PUSH uninstal.004E0B8C 004E0B1B . 64:FF30 PUSH DWORD PTR FS:[EAX] 004E0B1E . 64:8920 MOV DWORD PTR FS:[EAX],ESP 004E0B21 . 833D 544E4E00 >CMP DWORD PTR DS:[4E4E54],0 004E0B28 . 75 16 JNZ SHORT uninstal.004E0B40 004E0B2A . B9 100C4E00 MOV ECX,uninstal.004E0C10 ; ASCII "Unable to load lockdll.dll,Please re-install this software." 3. This code looks a little odd. Notice that it loads lockdll.dll immediately: CODE 004E0B04 . 68 FC0B4E00 PUSH uninstal.004E0BFC ; /FileName = "lockdll.dll" 004E0B09 . E8 565EF2FF CALL <JMP.&kernel32.LoadLibraryA> ; \LoadLibraryA 4. As it turns out the uninstaller.exe program is basically a frontend for the lockdll.dll. Go ahead and Right-Click->Search for->All referenced text strings. Now try and find the invalid registration key message we got earlier. It is not even located in the uninstaller.exe. 5. What we want to do is continue running the program until the lockdll.dll is loaded. To do this Choose Options and then from the drop down menu choose Debugging Options. Choose the Events tab and check Break on New Module (DLL). Press Okay 6. Press Run and you will break, the executable modules window should have opened up with all the newly loaded modules in RED. If you do not see lockdll.dll. Press Run again. 7. When you see lockdll.dll appear in Red in the executable modules list, select the line an Double click it. You will find yourself here: CODE 01591000 04 10 ADD AL,10 01591002 59 POP ECX 01591003 0103 ADD DWORD PTR DS:[EBX],EAX 01591005 07 POP ES ; Modification of segment register 01591006 42 INC EDX 01591007 6F OUTS DX,DWORD PTR ES:[EDI] ; I/O command 01591008 6F OUTS DX,DWORD PTR ES:[EDI] ; I/O command 01591009 6C INS BYTE PTR ES:[EDI],DX ; I/O command 0159100A 65:61 POPAD ; Superfluous prefix 0159100C 6E OUTS DX,BYTE PTR ES:[EDI] ; I/O command 0159100D 0100 ADD DWORD PTR DS:[EAX],EAX 8. Right click and choose Analysis->Analyse code. The garbage you see above will now become: CODE 01591000 . 04105901 DD lockdll.01591004 01591004 03 DB 03 01591005 . 07 DB 07 01591006 . 42 6F 6F 6C 65>ASCII "Boolean" 0159100D 01 DB 01 0159100E 00 DB 00 9. Now that we are inside the lockdll, we are going to search for the invalid registration key string. Right-Click->Search For->All referenced text strings 10. In the new Strings window Right-Click->Search for Text. And in the new box type in "The Registration code" without the quotes. Make sure Case Sensitive is UNchecked and Entire Scope IS checked. Press Okay. 11. You will be here: CODE 01605F00 MOV EAX,lockdll.0160601C ASCII "The registration code you entered is invalid. Please check the code to make sure that it was entered correctly." 12. Looking up a little from this line you will see some other strings that look very interesting: CODE 016058DB MOV EDX,lockdll.016059DC ASCII "Setup" 016058EC PUSH lockdll.016059EC ASCII "\Software\GlarySoft" 016058F5 MOV ECX,lockdll.01605A08 ASCII "Key" 016058FA MOV EDX,lockdll.016059DC ASCII "Setup" 13. Directly below those you see a string that looks like: xxxxx-xxxxx-xxxxx. I won't post it here so you will have to find it yourself. 14. Now you can try entering this key in to test out if it is correct. But we are going to do it a little differently. Go back to this line in the text strings and double click it: CODE Text strings referenced in lockdll:CODE, item 4377 01605F00 MOV EAX,lockdll.0160601C ASCII "The registration code you entered is invalid. Please check the code to make sure that it was entered correctly." 15. You will find yourself here, Scroll up until your code matches mine: CODE 01605EEA |. 8B55 F0 MOV EDX,DWORD PTR SS:[EBP-10] 01605EED |. 58 POP EAX 01605EEE |. E8 59E5F8FF CALL lockdll.0159444C;***Tests the Serial*** 01605EF3 |. 74 33 JE SHORT lockdll.01605F28;***Jumps if serial is correct*** 01605EF5 |. 6A 00 PUSH 0 ; /Arg1 = 00000000 01605EF7 |. 66:8B0D 106060>MOV CX,WORD PTR DS:[1606010] ; | 01605EFE |. 33D2 XOR EDX,EDX ; | 01605F00 |. B8 1C606001 MOV EAX,lockdll.0160601C ; |ASCII "The registration code you entered is invalid. Please check the code to make sure that it was entered correctly." 01605F05 |. E8 DA3DFBFF CALL lockdll.015B9CE4 ; \lockdll.015B9CE4 01605F0A |. 8B83 FC020000 MOV EAX,DWORD PTR DS:[EBX+2FC] 16. Put a breakpoint on the Call that tests our serial: CODE 01605EEE |. E8 59E5F8FF CALL lockdll.0159444C;***Tests the Serial*** 17. Press Run and the nag screen will pop up. Enter any name and key, press Okay. 18. You will break on the CALL lockdll.0159444C. Press Step Into. 19. Looking at the registers we see that they contain our real serial as well as our entered serial: CODE EAX 016510C0 ASCII "111111111111111" ECX 016510D4 EDX 016510DC ASCII "xxxxx-xxxxx-xxxxx" EBX 01650B80 ESP 0012ECC0 EBP 0012ECF8 ESI 015C0A94 lockdll.015C0A94 EDI 0012EE7C EIP 0159444C lockdll.0159444C 20. Since I wanted to make this tutorial about something more than just finding a hardcoded serial. I have commented the code so you will understand how this serial check works: CODE 0159444A 8BC0 MOV EAX,EAX 0159444C /$ 53 PUSH EBX ; PUSHES THE REGISTERS 0159444D |. 56 PUSH ESI ; SO THEY CAN BE RESTORED 0159444E |. 57 PUSH EDI ; AFTER CHECKING THE SERIAL 0159444F |. 89C6 MOV ESI,EAX ; MOVES OUR ENTERED SERIAL INTO ESI 01594451 |. 89D7 MOV EDI,EDX ; MOVES OUR REAL SERIAL INTO EDI 01594453 |. 39D0 CMP EAX,EDX ; CHECKS IF EAX AND EDX POINT TO DIFFERENT LOCATIONS 01594455 |. 0F84 8F000000 JE lockdll.015944EA ; JUMPS IF THEY POINT TO SAME LOCATION 0159445B |. 85F6 TEST ESI,ESI ; CHECKS IF ESI IS ZERO 0159445D |. 74 68 JE SHORT lockdll.015944C7 ; JUMPS IF ESI IS ZERO 0159445F |. 85FF TEST EDI,EDI ; CHECKS IF EDI IS ZERO 01594461 |. 74 6B JE SHORT lockdll.015944CE ; JUMPS IF EDI IS ZERO 01594463 |. 8B46 FC MOV EAX,DWORD PTR DS:[ESI-4] ; MOVES THE LENGTH OF ENTERED SERIAL INTO EAX 01594466 |. 8B57 FC MOV EDX,DWORD PTR DS:[EDI-4] ; MOVES THE LENGTH OF REAL SERIAL INTO EDX 01594469 |. 29D0 SUB EAX,EDX ; SUBTRACTS EDX FROM EAX 0159446B |. 77 02 JA SHORT lockdll.0159446F ; JUMPS IF EAX WAS GREATER 0159446D |. 01C2 ADD EDX,EAX ; ADDS EAX TO EDX SO LENGTH TO TEST IS EQUAL 0159446F |> 52 PUSH EDX ; PUSHES EDX ONTO THE STACK 01594470 |. C1EA 02 SHR EDX,2 ; SHIFTS THE BITS TO THE RIGHT BY 2 01594473 |. 74 26 JE SHORT lockdll.0159449B ; JUMPS IF SHR MADE EDX BECOME 0 01594475 |> 8B0E /MOV ECX,DWORD PTR DS:[ESI] ; MOVES THE FIRST 4 CHARS OF ENTERED SERIAL INTO ECX 01594477 |. 8B1F |MOV EBX,DWORD PTR DS:[EDI] ; MOVES FIRST 4 CHARS OF REAL SERIAL INTO EBX 01594479 |. 39D9 |CMP ECX,EBX ; COMPARES FIRST 4 CHARS OF THE SERIALS 0159447B |. 75 58 |JNZ SHORT lockdll.015944D5 ; JUMPS IF THEY ARE NOT EQUAL 0159447D |. 4A |DEC EDX ; DECREASE EDX BY 1 0159447E |. 74 15 |JE SHORT lockdll.01594495 ; JUMP IF EDX IS ZERO 01594480 |. 8B4E 04 |MOV ECX,DWORD PTR DS:[ESI+4] ; MOVES NEXT 4 CHARS OF ENTERED SERIAL INTO ECX 01594483 |. 8B5F 04 |MOV EBX,DWORD PTR DS:[EDI+4] ; MOVES NEXT 4 CHARS OF REAL SERIAL INTO EBX 01594486 |. 39D9 |CMP ECX,EBX ; COMPARES THE NEXT 4 CHARS OF THE SERIALS 01594488 |. 75 4B |JNZ SHORT lockdll.015944D5 ; JUMPS IF THE COMPARED CHARS ARE NOT EQUAL 0159448A |. 83C6 08 |ADD ESI,8 ; ADDS 8 TO THE VALUE IN ESI 0159448D |. 83C7 08 |ADD EDI,8 ; ADDS 8 TO THE VALUE IN EDI 01594490 |. 4A |DEC EDX ; SUBTRACTS 1 FROM EDX 01594491 |.^75 E2 \JNZ SHORT lockdll.01594475 ; JUMPS BACK TO THE TOP OF THE COMPARE LOOP IF EDX IS NOT ZERO 01594493 |. EB 06 JMP SHORT lockdll.0159449B ; IF WE MADE IT THROUGH THE WHOLE LOOP WE JUMP 21. Looking at the comments will help walk you through the comparison routine of this program. The program enters our two serials into ESI and EDI. It then compares them by reading the first 4 characters into ECX and EBX. Notice that the Characters are stored in ECX and EDX as Hexadecimal values. 22. Example: My serial was 11111111111, so the first 4 Characters are saved in ECX as 31313131. Because 31 is the hexadecimal value of ASCII "1". 23. Also the characters are stored in what is called "little endian format". This essentially means that the first character from the serial is stored in the LOWEST bytes of ECX. (The lowest byte is the byte farthest to the right in the register, see Beginner Tutorial #5 for more information on the registers). 24. Example: if my serial was 1234. It would be stored in ECX as: CODE Hexadecimal: 34333231 Decimal: 4 3 2 1 25. Another thing I want to cover is: CODE 0159448A |. 83C6 08 |ADD ESI,8 ; ADDS 8 TO THE VALUE IN ESI You noticed that the routine compares the first 4 characters, then the next 4 characters. Contrary to what is commonly said (even by me in this tutorial) ESI and EDI do not contain the actual serials, instead they point to a memory location that contains the serials. 8 is added to each register so that the registers now point to (beginning of the serial + 8 BYTES). So now the registers point 8 characters into the serials. 26. The other thing I want to cover is this line: CODE 01594470 |. C1EA 02 SHR EDX,2 ; SHIFTS THE BITS TO THE RIGHT BY 2 27. What the SHR instruction does is moves the BITS to the right. Moving the lower order bits into the Carry Flag (You do not need to know about the Carry Flag right now). 28. Example: SHR EDX,2 We will say that the value of EDX is F F written in decimal as 1111 So we are going to shift those 1's to the right 2 times. 1 time ->111 The last 1 is set as CF 2nd time ->11 The last 1 is set as CF So in decimal we now have 0011 Which in decimal is 3 So EDX now contains 3 Now why do we even use SHR? Because it is a quick way to divide by the base number. For everyday life we use decimal format, that means our base number is 10. So in decimal Assume we have the number 1300. Shifting 1300 right will make it 130. Which is the same as dividing by 10 Shifting 1300 right 2 times will make it 13. Which is the same as dividing it by 10^2 What if we had 1303? Well for that we go back to elementary math where we did division with remainders 1303/10 = 130 with a remainder of 3 Shifting 1303 right will make it 130. And the 3 is our remainder So back to Binary, Which has a base of 2 Assume we had 100. Which is 4 in decimal So 4 divided by the base number 2 equals 2 Which is the same as Shifting 100 right once and making it 10 Now what if we had 101. That is 5 in decimal 5/2 = 2 remainder of 1 We get the same result by shifting the bits 101 right once 101 becomes 10 and the 1 bit that was shifted off (our remainder) goes into the Carry Flag So SHR NUM,X Divides NUM by 2^X 29. Stepping through the code you can see your serial get compared with the serial we found in the strings section. So you now know that we were correct in assuming that the serial was hardcoded. Go ahead and press RUN, you will get the invalid registration box. 30. This time, enter in your name and the hardcoded serial. Press Okay, and you will register the program!! 31. If you are curious, step through the compare routine again and see what jumps are taken/or not taken with a correct serial. 32. Hope you enjoyed this little tutorial and learned something out of it as well. |
Addendum: |
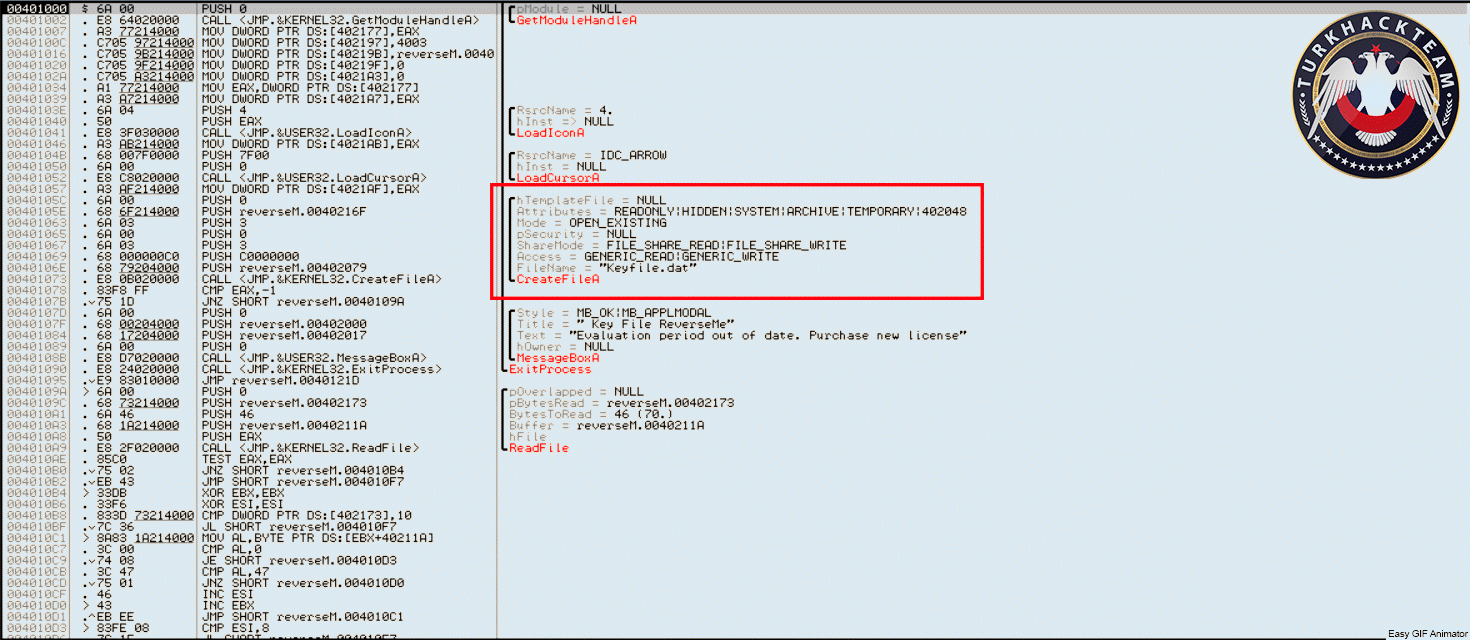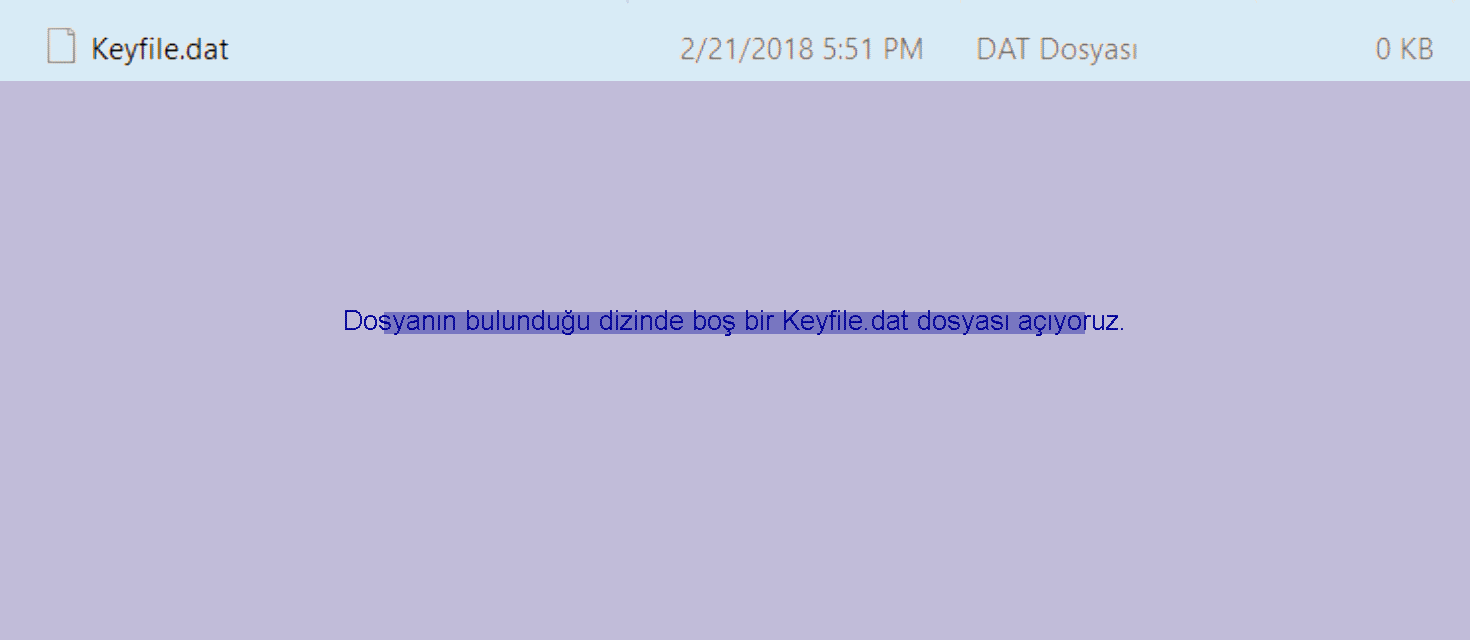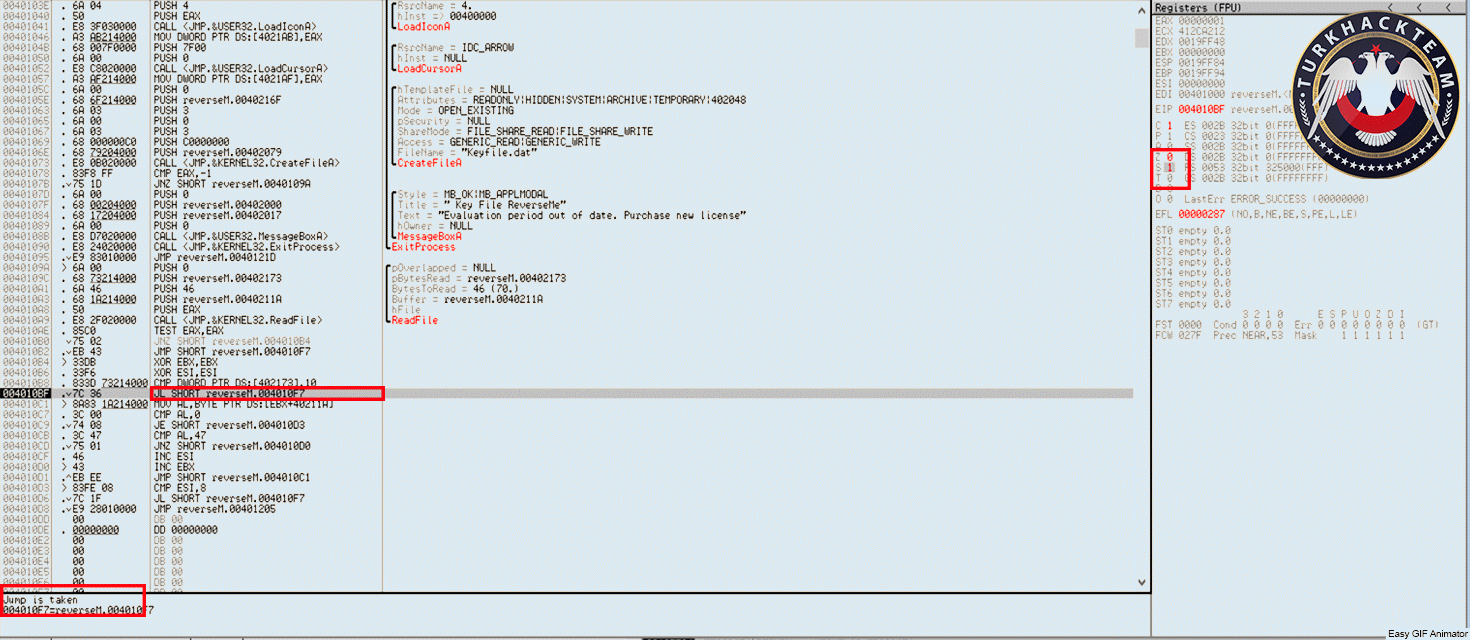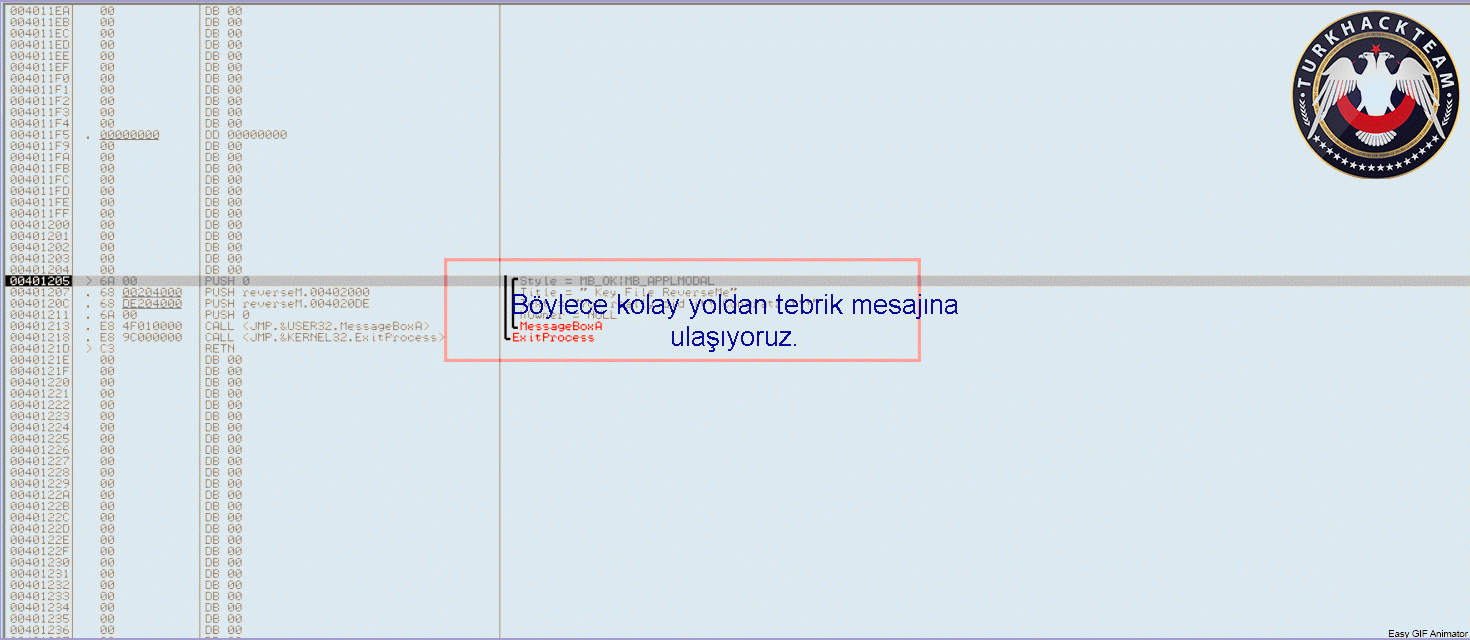
With the release of the newer version it is tougher to fish a serial, however you can easily patch the lockdll.dll. The following is how you can fix lockdll to always think you are registered.
CODE 012F606B |. E8 A8F6FFFF CALL lockdll.012F5718 ****THIS CALL****** 012F6070 |. 84C0 TEST AL,AL 012F6072 |. 75 33 JNZ SHORT lockdll.012F60A7 012F6074 |. 6A 00 PUSH 0 ; /Arg1 = 00000000 012F6076 |. 66:8B0D 7C612F>MOV CX,WORD PTR DS:[12F617C] ; | 012F607D |. 33D2 XOR EDX,EDX ; | 012F607F |. B8 88612F01 MOV EAX,lockdll.012F6188 ; |ASCII "The registration code you entered is invalid. Please check the code to make sure that it was entered correctly." 012F6084 |. E8 8F3AFBFF CALL lockdll.012A9B18 ; \lockdll.012A9B18 2. Step into that and you are here: CODE 012F5718 /$ 55 PUSH EBP 012F5719 |. 8BEC MOV EBP,ESP 012F571B |. B9 09000000 MOV ECX,9 012F5720 |> 6A 00 /PUSH 0 012F5722 |. 6A 00 |PUSH 0 012F5724 |. 49 |DEC ECX 012F5725 |.^75 F9 \JNZ SHORT lockdll.012F5720 012F5727 |. 53 PUSH EBX 012F5728 |. 56 PUSH ESI 3. Scroll down to the RETN and set a BP: CODE 012F5AAD |. 64:8910 MOV DWORD PTR FS:[EAX],EDX 012F5AB0 |. 68 CA5A2F01 PUSH lockdll.012F5ACA ; ASCII "‹Ã^[‹å]Ã" 012F5AB5 |> 8D45 B8 LEA EAX,DWORD PTR SS:[EBP-48] 012F5AB8 |. BA 12000000 MOV EDX,12 012F5ABD |. E8 A2E5F8FF CALL lockdll.01284064 012F5AC2 \. C3 RETN ****SET A BP**** 4. Run the program until you hit that BP 5. Press Step over you'll be here: (If you only see junk code try removing or applying analysis) CODE 012F5ACA 8BC3 MOV EAX,EBX 012F5ACC 5E POP ESI 012F5ACD ? 5B POP EBX 012F5ACE ? 8BE5 MOV ESP,EBP 012F5AD0 ? 5D POP EBP 012F5AD1 ? C3 RETN 6. That MOV EAX,EBX sets the AL to registered or not registered. 7. Assemble that line to MOV AL,01 CODE 012F5ACA B0 01 MOV AL,1 012F5ACC 5E POP ESI 012F5ACD ? 5B POP EBX 012F5ACE ? 8BE5 MOV ESP,EBP 012F5AD0 ? 5D POP EBP 012F5AD1 ? C3 RETN
At the time this was written, this method of patching could be applied to ALL glarysoft products. Patching Lockdll.dll in each softwares folder would allow you to "register" all the publishers software. I do not know if this continues to be true, however if it is true a simple Search and Replace patcher can be made to patch any glarysoft products.
|
Conclusion: |
| I used this particular program purely as a demonstration. If you like the program and are going to use it please purchase it. [Nilrem] [JDog45] [Shub - Nigurrath] [MaDMAn_H3rCuL3s] [Ferrari] [Kruger] [Teerayoot] [R@dier] [ThunderPwr] [Eggi] [EJ12N] [Stickman 373] [Bone Enterprise] [Condzero] [Cl0ud] Thanks to all the people who take time to write tutorials. Thanks to all the people who continue to develop better tools. Thanks to Diablo2oo2 for his excellent patcher Thanks to Exetools and Woodmann for being a great place of learning. Thanks also to The Codebreakers Journal, and the Anticrack forum. If you have any suggestions, comments or corrections email me: Gabri3l2003[at]yahoo.com |