Hi, I want to present two different methods one can use to change the text which appears on the button.
1. Debugging using dnSpy - This method does not require any unpacking. Steps:
- Eazfuscator always encrypts strings before applying the virtualization. This means that the text in the button is encrypted.
- Since we know the string is encrypted by Eazfuscator, we find the string decrypter method.
- In order to find the string decrypter, first we navigate to entrypoint (dnSpy has a handy context menu action for this). Entrypoint looks a bit like this:
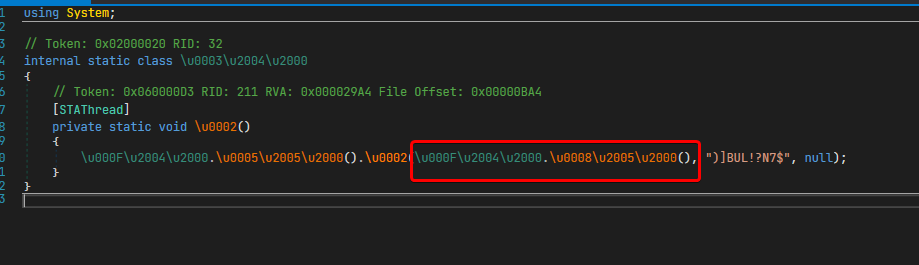
Then we navigate to the method highlighted in the image. This class should contain the following code:
Then finally we navigate to the class highlighted in the image and find a method which looks similar to this:
This is the string decrypter. After we located this method we can go to the next step - In order to hijack and modify the result we need to place breakpoints strategically. In this case i set a breakpoint on the last occurrence of "return text;` located at the end of the method.
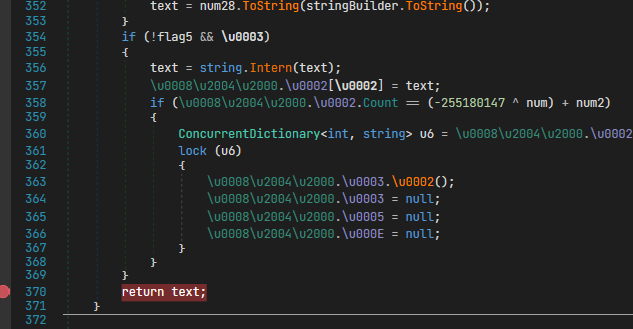
- Now that we have set breakpoints, we can move forward to actually debugging the application. To do that we press F5 on the keyboard to start debugging and click OK on the dialog prompt.
- A breakpoint is hit, in the Locals window we see that our return variable "text" has a value of what looks like some cryptic string.
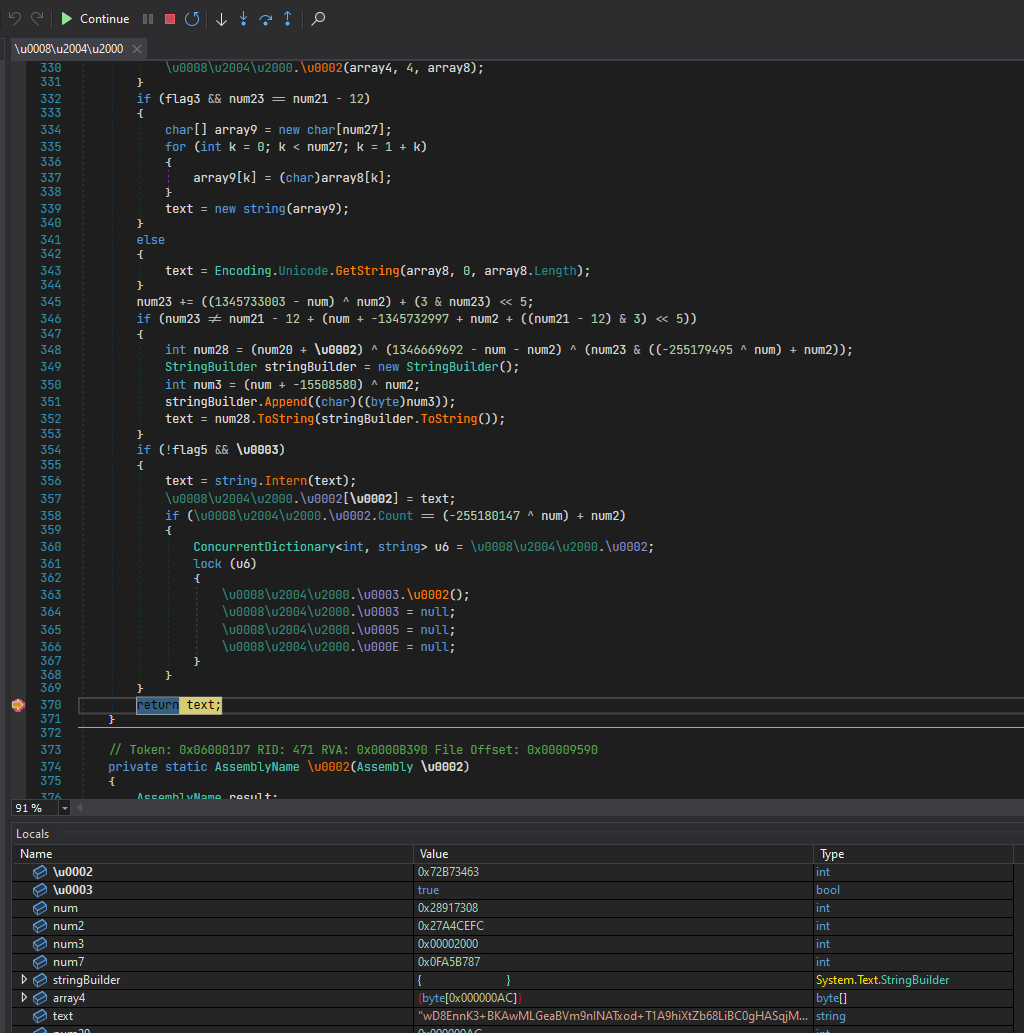
We hit F5 to continue the debugging process. - Our breakpoint was hit again, this time the string is ".ctor". We continue to debug using the F5 key.
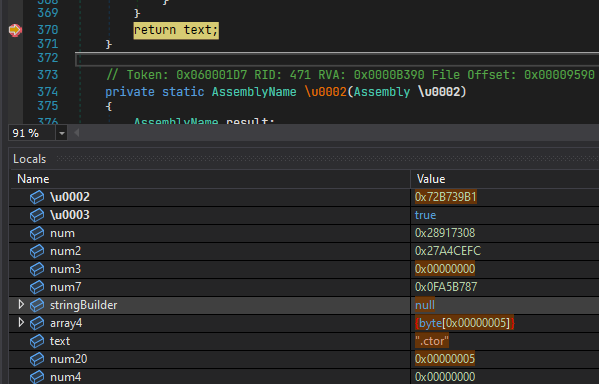
- Continue to debug until the value of "text" is "CHANGE MY MESSAGE". Now we can get to changing the value. Let's right click the "text" local and select "Edit Value".
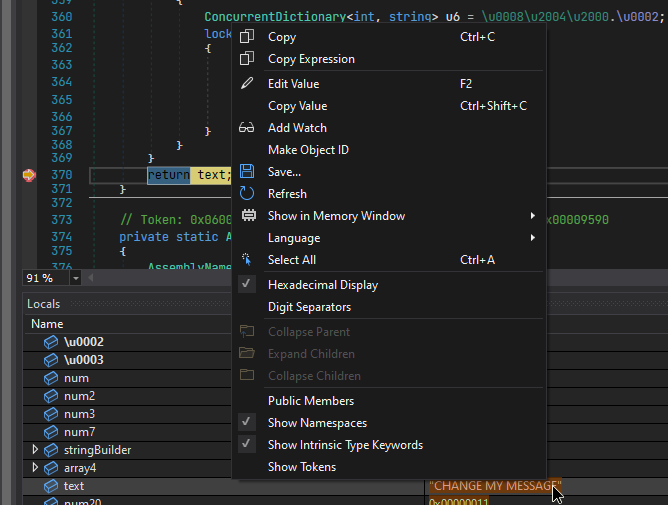
The context menu disappears and we can now edit the value.
We type in out new value,
And press enter.
Success! the value is now changed! - We continue to debug the application until the main window appears.
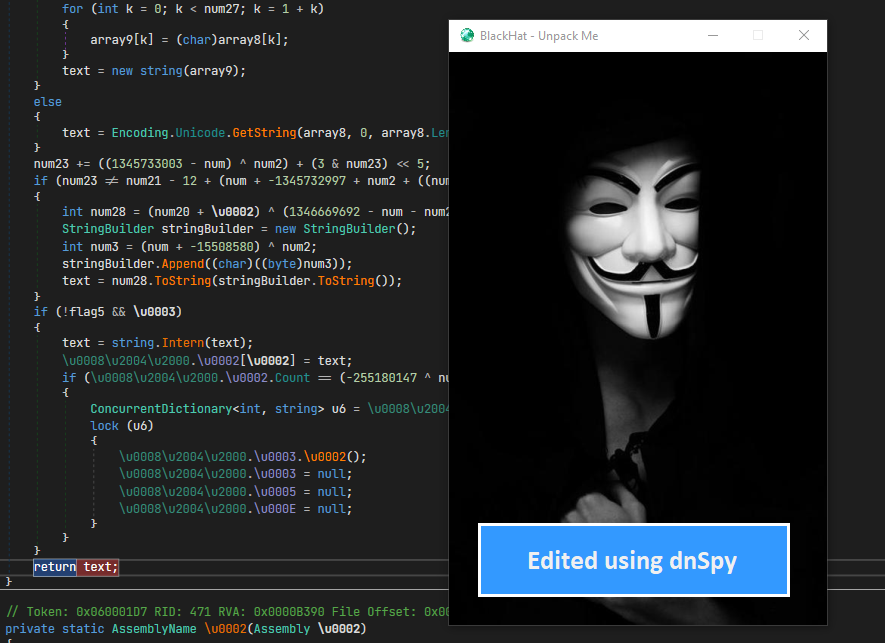
- We have successfully modified the message without modifying the file at all. Using the same method we can press the button and modify the text displayed in the message box.
2. Deobfuscate and devirtualize the file - This is much much harder and requires custom tools to be developed.
- After deobfuscating and renaming the file using a renamer of our choice, we open the file in dnSpy and find the code we need to change. As the virtualization has been removed this is quite trivial.
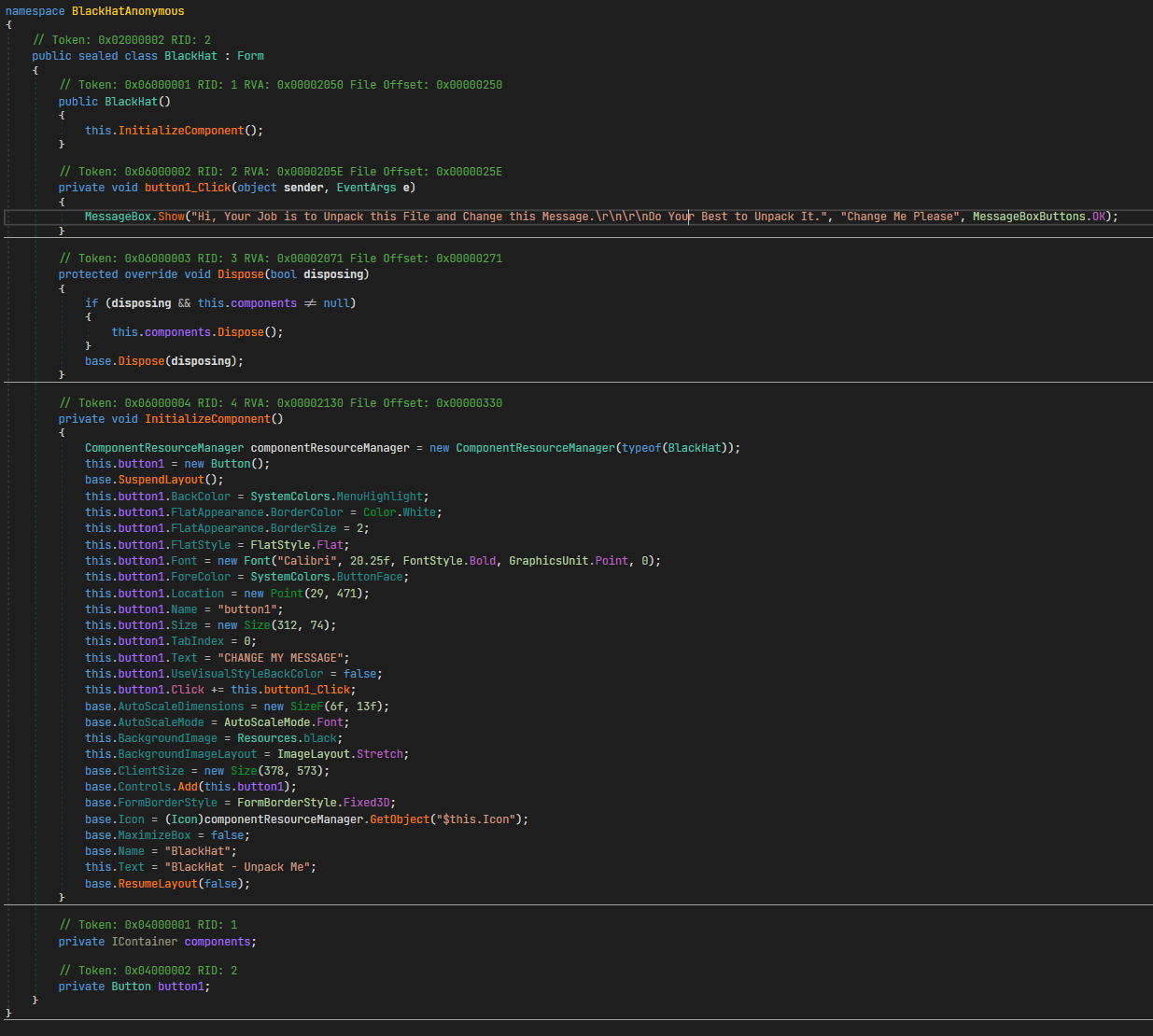
- We can right click the string, select "Edit IL Instructions" and modify the operand of the "ldstr" instruction highlighted to our string.
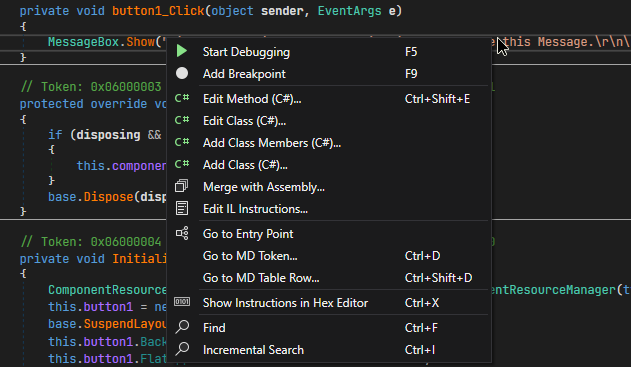
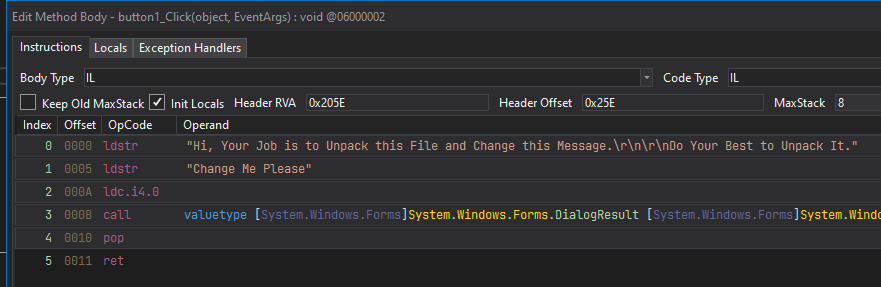
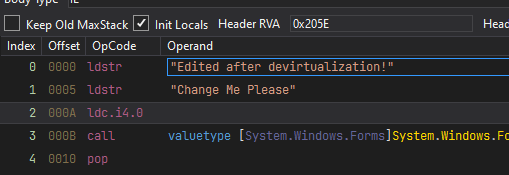
- We can then save the file by going to File -> Save Module and selecting the location and pressing OK.
- Running the modified file results in the message being changed to what we wanted.
I hope my rather easy to follow guide (for the first method) is beneficial to some people who want to learn other methods besides unpacking which can be used to change the behavior of a application!
Fully deobfuscated, devirtualized and renamed file is attached below.
More on unpacking and devirtualizing Eazfuscator:
For the basic protection public code is already available, e.g. EazFixer
For devirtualization, no public tools exist. Eazfuscator is pretty much a 1:1 VM so it is not very hard to restore. Only real annoyance is the equality comparison obfuscation and code encryption which Gapotchenko refers to as "homomorphic encryption" when it is really not that. It just encrypts both sides of a comparison and uses the decrypted value as the key of the code following the comparison.
Hiç yorum yok:
Yorum Gönder