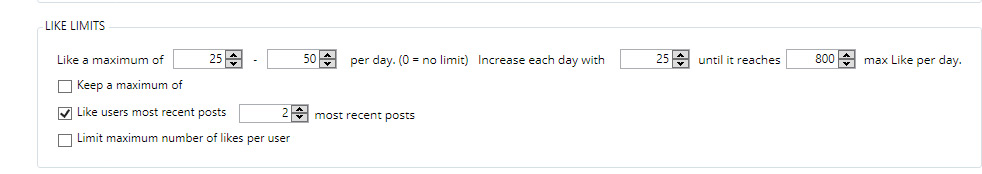DRAGONBLOOD
Analysing WPA3's Dragonfly Handshake
By Mathy Vanhoef (NYUAD) and Eyal Ronen (Tel Aviv University & KU Leuven)
INTRODUCTION
Currently, all modern Wi-Fi networks use WPA2 to protect transmitted data. However, because WPA2 is more than 14 years old, the Wi-Fi Alliance recently announced the new and more secure WPA3 protocol. One of the main advantages of WPA3 is that, thanks to its underlying Dragonfly handshake, it's near impossible to crack the password of a network. Unfortunately, we found that even with WPA3, an attacker within range of a victim can still recover the password of the network. This allows the adversary to steal sensitive information such as credit cards, password, emails, and so on, when the victim uses no extra layer of protection such as HTTPS. Fortunately, we expect that our work and coordination with the Wi-Fi Alliance will allow vendors to mitigate our attacks before WPA3 becomes widespread.
The Dragonfly handshake, which forms the core of WPA3, is also used on certain Wi-Fi networks that require a username and password for access control. That is, Dragonfly is also used in the EAP-pwd protocol. Unfortunately, our attacks against WPA3 also work against EAP-pwd, meaning an adversary can even recover a user's password when EAP-pwd is used. We also discovered serious bugs in most products that implement EAP-pwd. These allow an adversary to impersonate any user, and thereby access the Wi-Fi network, without knowing the user's password. Although we believe that EAP-pwd is used fairly infrequently, this still poses serious risks for many users, and illustrates the risks of incorrectly implementing Dragonfly.
The technical details behind our attacks against WPA3 can be found in our detailed research paper titled Dragonblood: A Security Analysis of WPA3's SAE Handshake. The details of our EAP-pwd attacks are explained on this website.
Coordinated Disclosure
We collaborated with the Wi-Fi Alliance and CERT/CC to notify all affected vendors in a coordinated manner, and helped with implementing backwards-compatible countermeasures. Please check with your vendors for updates. The Wi-Fi Alliance has published a press release, and hostap published advisories and patches. We will post more information about CVEs and available patches as they become public.
FLAWS IN WPA3
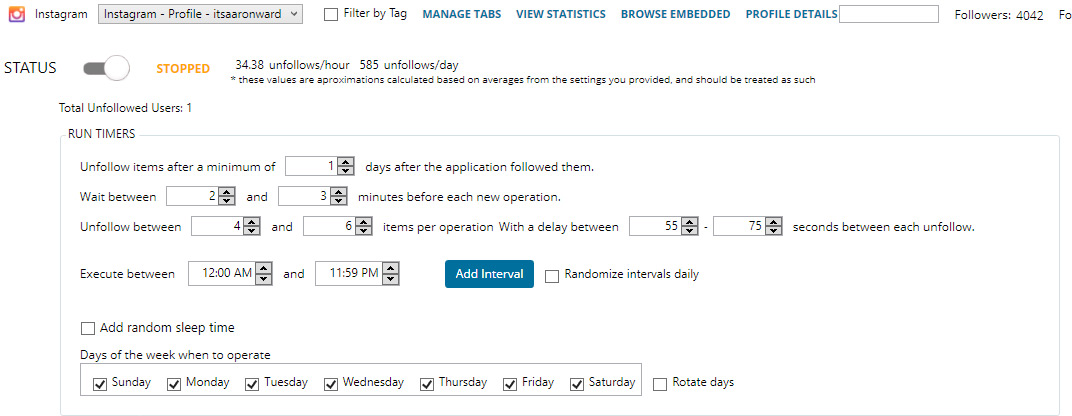
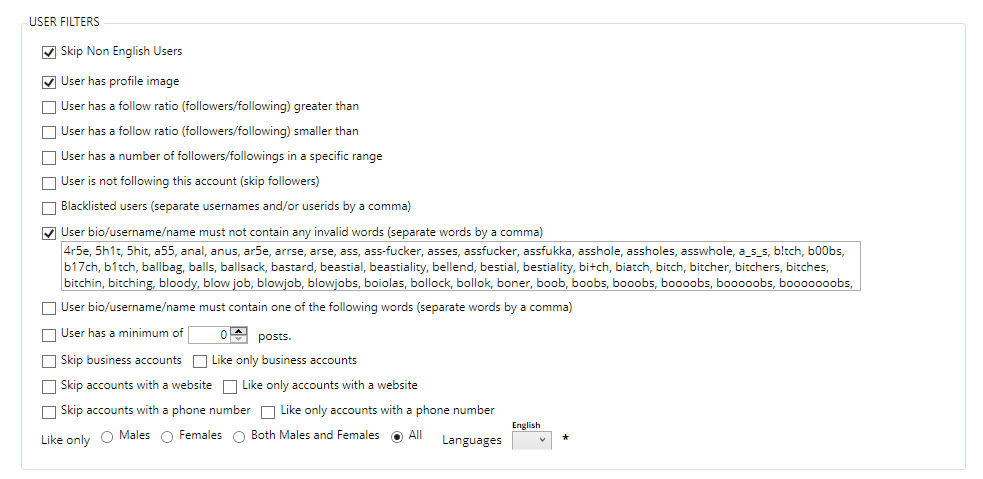
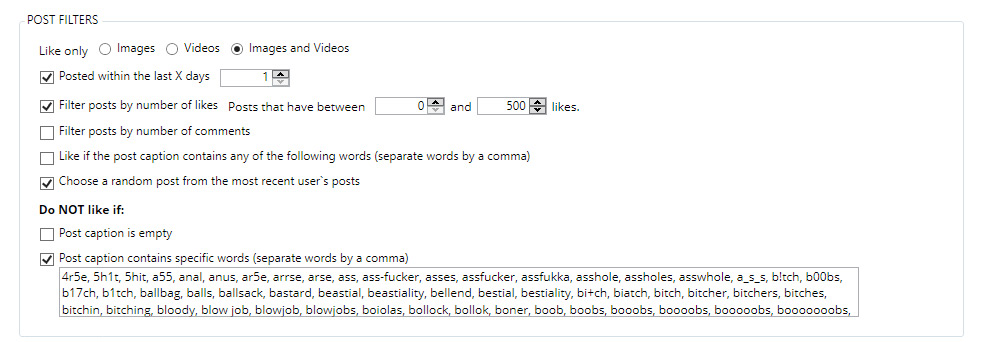
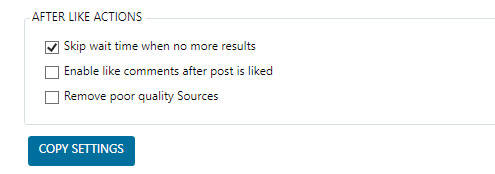
The design flaws we discovered can be divided in two categories. The first category consists of downgrade attacks against WPA3-capable devices, and the second category consists of weaknesses in the Dragonfly handshake of WPA3, which in the Wi-Fi standard is better known as the Simultaneous Authentication of Equals (SAE) handshake. The discovered flaws can be abused to recover the password of the Wi-Fi network, launch resource consumption attacks, and force devices into using weaker security groups. All attacks are against home networks (i.e. WPA3-Personal), where one password is shared among all users. Summarized, we found the following vulnerabilities in WPA3:
- CERT ID #VU871675: Downgrade attack against WPA3-Transtition mode leading to dictionary attacks.
- CERT ID #VU871675: Security group downgrade attack against WPA3's Dragonfly handshake.
- CVE-2019-9494: Timing-based side-channel attack against WPA3's Dragonfly handshake.
- CVE-2019-9494: Cache-based side-channel attack against WPA3's Dragonfly handshake.
- CERT ID #VU871675: Resource consumption attack (i.e. denial of service) against WPA3's Dragonfly handshake.
The resulting attacks are efficient and low cost. For example, the downgrade attacks can be exploited using existing WPA2 cracking tools and hardware. The side-channel vulnerabilities can, for instance, be abused to brute-force all 8-character lowercase passwords with as little as 125$ worth of Amazon EC2 instances.
Below we will give high-level descriptions of these attacks, and for the full technical details we refer to our paper.
Downgrade & Dictionary Attack Against WPA3-Transition
Our first attack exploits the backward compatibility of WPA3. To accommodate older clients that only support WPA2, and to motivate the transition towards WPA3, a WPA3-Transition mode was created. In this mode a Wi-Fi network supports the usage both WPA3 and WPA2 with an identical password. We found that an adversary can create a rogue network and force clients that support WPA3 into connecting using WPA2. The captured partial WPA2 handshake can be used to recover the password of the network (using brute-force or dictionary attacks). No man-in-the-middle position is required to perform this attack.
Apart from the above design flaw, we also discovered that the Samsung Galaxy S10 and the iNet Wireless Daemon are affected by implementation-specific downgrades. Even when these clients connect with a WPA3-only network, an adversary can still force them into using WPA2. This allows an adversary to recover the network's password using brute-force or dictionary attacks.
Security Group Downgrade Attack
We also discovered a downgrade attack against the WPA3's Dragonfly handshake itself, where the victim can be forced to use a weak security group. The device that initiates the handshake (typically the client) sends a commit frame that includes the security group it wishes to use. If the AP does not support this group, it responds with a decline message, forcing the client to send a commit frame using another group. This process continues until a security group is found that is supported by both sides. An attacker can impersonate an AP and forge decline messages to force clients into choosing a weak security group.
Timing-Based Side-Channel Attack
With WPA3 it is considered infeasible for an adversary to recover the password of a Wi-Fi network. Unfortunately, we discovered that the amount of times it takes for an AP to respond to commit frames may leak information about the password. When the AP uses security groups based on elliptic curves, which all WPA3 devices are required to support, no timing information is leaked. However, when the AP supports the optional multiplicative security groups modulo a prime (MODP groups), the response time depends on the password being used. An adversary can abuse this information to perform a dictionary attack, by simulating how much time it would take for the AP to process each password, and comparing this to observed timings.
Cache-Based Side-Channel Attack
When an adversary is able to observe memory access patterns on a victim's device when it's constructing the commit frame of a Dragonfly handshake, these memory access patterns reveal information about the password being used. Observing these patterns is possible if the adversary controls any application on the victim's device, and may even be possible when the adversary controls JavaScript code in the victim's browser. The leaked patterns can be used to perform a dictionary attack, by simulating the memory access patterns associated to a guessed password, and comparing this to the measured access patterns.
Denial-of-Service Attack
The device that initiates the Dragonfly handshake starts by sending a commit frame. Processing this frame and generating an answer is computationally expensive, especially if defenses against (already known) side-channel attacks are implemented. Although WPA3 contains a cookie-exchange method to prevent attackers from forging commit frames using fake MAC addresses, it is trivial to bypass. As a result, an attacker can overload Access Points (APs) by generating as little as 16 forged commit frames per second. This resource consumption attack causes a high CPU usage on the AP, drains its battery, prevents or delays other devices from connecting to the AP using WPA3, and may halt or slowdown other functionality of the AP as well.
Although the attack can be mitigated by processing the commit frame in a low-priority background thread, variants of the attack remain possible. Depending on the precise defense that vendors implement, either it will still be possible to trigger a high CPU usage on the AP, or it will still be possible to prevent or delay other devices from connecting to the AP using WPA3.
FLAWS IN EAP-PWD
Due to the severity of some of our (implementation-specific) attacks against EAP-pwd, we will briefly delay the release of the full details of the vulnerabilities that we discovered. Please use this short time window to update your devices, we plan to provide the full details in as little as a few hours.
PAPER
Our research paper behind the attack is titled Dragonblood: A Security Analysis of WPA3's SAE Handshake. The paper focusses on all discoveries related to WPA3. In other words, the recent discoveries concerning the EAP-pwd protocol are not discussed in this paper.
TOOLS
All our tools are made available so other researchers can replicate our results. These tools are not designed to attack your neighbor's WPA3, and our hope is that vendors mitigate these attacks.
- Dragonslayer: performs invalid curve attacks against EAP-pwd clients and server. These attacks bypass authentication: an adversary only needs to possess a valid username.
- Dragondrain: this tool can be used to test wether, or to which extend, an Access Point is vulnerable to denial-of-service attacks against WPA3's SAE handshake.
- Dragontime: this is an experimental tool to perform timing attacks against the SAE handshake if MODP group 22, 23, or 24 are supported. Note that most WPA3 implementations by default do not enable these groups.
- Dragonforce: this is an experimental tool which takes the information recovered from our timing or cache-based attacks, and performs a password partitioning attack. This is similar to a dictionary attack.
In practice the main risks for WPA3 are downgrade attacks, and possible timing attacks against resource-constrained devices. The authentication bypass attacks against EAP-pwd that are implemented in Dragonslayer are also security critical in practice. Considering the other attacks are non-trivial in practice, and assuming vendors will implement defenses against them, we expect that your neighbour won't abuse them to attack you.
Q&A
Why aren't there more Q&A entries?
We discovered certain implementation-specific vulnerabilities in the EAP-pwd protocol fairly late during the embargo period. In the past days we focussed on helping vendors write and audit patches for EAP-pwd to prevent the most critical attacks, instead of working on the webiste. We will further update the website over the next hours and days!